Hardware Reference
In-Depth Information
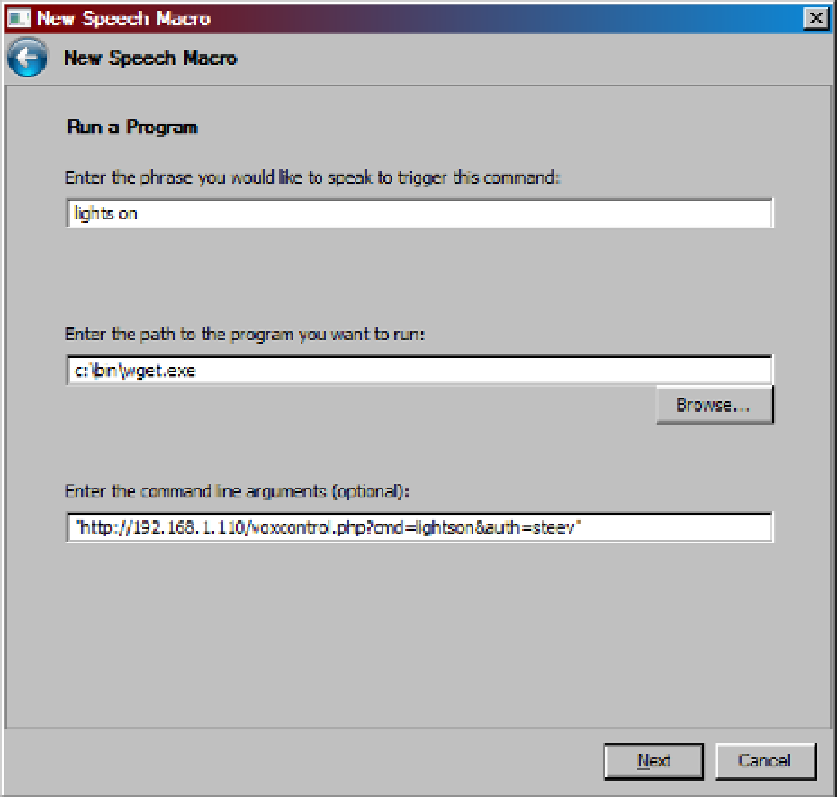
Figure 5-1.
Preparing a voice macro under Vista. (Used with permission from Microsoft.)
Naturally, the
auth
keyword is a misnomer, as anyone (from anywhere) could request the same page and trigger
the command. However, by using the machine's local IP address, the request will never leave your intranet, and by
locking the Windows machine down, no one else could discover the secret key.
7
So, once again, you're vulnerable only
to those with physical access to the machines (also known as your family, which has access to the light switch itself )!
From here, the server code is trivial and expected:
<?php
$cmd = $_GET['cmd'];
if ($cmd == "lightson") {
system("heyu turn bedroom_light on");
}
9OUCANALSOSETUPAVIRTUALHOSTTORESPONDONLYTOMACHINESONYOURINTRANETSOTHATANYREQUESTSFROMOUTSIDEWOULDBEUNABLE
TOACCESSTHISFILE
Search WWH ::

Custom Search