Java Reference
In-Depth Information
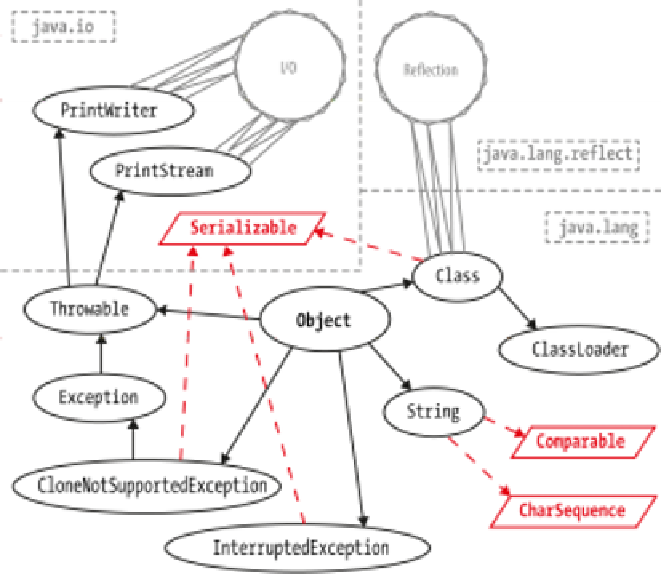
Figure 11-1. Transitive closure of types
This provides a “pinch point”—the only way to create a new class is to use the func‐
tionality provided by
Classloader
to load a class from a stream of bytes. By con‐
centrating on making classloading secure, we can constrain the attack surface that
needs to be protected.
One aspect of the JVM's design that is extremely helpful is that the JVM is a stack
machine—so all operations are evaluated on a stack, rather than in registers. The
stack state can be deduced at every point in a method, and this can be used to
ensure that the bytecode doesn't attempt to violate the security model.
Some of the security checks that are implemented by the JVM are:
• All the bytecode of the class has valid parameters.
• All methods are called with the right number of parameters of the correct static
types.
• Bytecode never tries to underflow or overflow the JVM stack.
• Local variables are not used before they are initialized.
• Variables are only assigned suitably typed values.