Database Reference
In-Depth Information
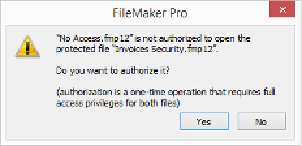
Figure 18-20. Even if a file is authorized for access to a protected file, you have to enter a [Full
Access] account name and password before creating a TO from the protected file. You see this mes-
sage when you first try to create a TO and again if you enter an account without full access priv-
ileges.
NOTE
The wording in the File Access dialog box is a little confusing. You can still create an EDS referen-
ce (
Defining Data Sources Using a Path
) to a protected file from an unauthorized file without a full
access password, but you can't create a TO from it, or use design functions to grab data from the
file.
Now open the authorized file (
Access.fmp12
—account name and password are both “ac-
cess”). Again, enter a full access password for the Invoice file. This time, enter the account
name and password you set up in the steps on
Managing Accounts
.
Ta-da! Your authorized
file can create TOs and then work with the file's external data normally.
Scripts and Security
Security and script writing intersect in two areas. First, you need to take into account the
level of access people have, and whether or not your scripts override some or all of their
privileges. Second, FileMaker lets you automate some of the security features described
earlier in this chapter with scripting. A handful of script steps are dedicated to security-re-
lated tasks, and this section shows you how to use them.
Detecting Privileges in a Script
The first way to handle security in your scripts is to deal with it directly. In the last section,
you learned how to check for extended privileges and take appropriate actions. If you want,
then you can check for specific privilege sets, or even specific account names: