Hardware Reference
In-Depth Information
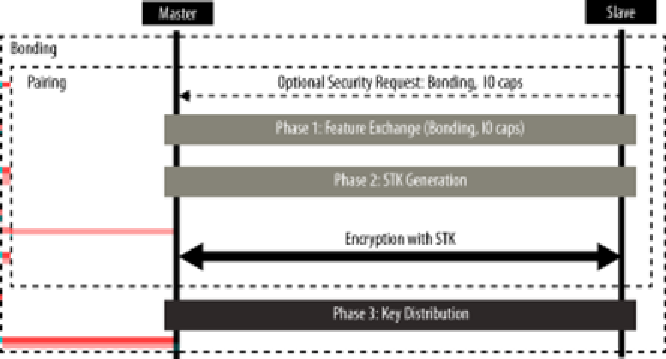
Figure 2-6. Pairing and Bonding sequences
Pairing Algorithms
A pairing procedure involves an exchange of Security Manager Protocol (SMP) packets
to generate a temporary encryption key called Short Term Key (STK) on both sides. The
last step of a
pairing
procedure (regardless of whether it will then continue into a security
key exchange and therefore a
bonding
procedure) is to encrypt the link with the previ‐
ously generated STK. During the packet exchange, the two peers negotiate one of the
following STK generation methods:
Just Works
The STK is generated on both sides, based on the packets exchanged in plain text.
This provides no security against
man-in-the-middle
(MITM) attacks.
Passkey Display
One of the peers displays a randomly generated, six-digit passkey and the other side
is asked to enter it (or in certain cases both sides enter the key, if no display is
available). This provides protection against MITM attacks and is used whenever
possible.
Out Of Band (OOB)
When using this method, additional data is transferred by means other than the
BLE radio, such as another wireless technology like NFC. This method also provides
protection against MITM attacks.
The SM specifies the following three types of security mechanisms that can be used to
enforce various levels of security while in a connection or during the advertising pro‐
cedure: