Cryptography Reference
In-Depth Information
rix. In this case, the resulting ciphertext would be completely immune to both Kasiski's method and to win-
dowed digraph and trigraph analysis, defeating all of the techniques previously developed.
However, using a small sequence of polyalphabetic and columnar transposition ciphers in sequence does not
make a cipher robust enough for modern use. Anyone who can guess which combination of techniques is being
used can easily combine several types of analysis at once. There are a fairly limited number of combinations of
these simple techniques to be used. And even so, these combinations could be easily broken by modern comput-
ing speeds. And finally, because most modern data that need to be encrypted are binary data from computers,
and not handwritten or typed messages, these techniques are ill-suited for most current needs.
4.3 Substitutions and Permutations
In Chapter 1 I discussed two useful tools:
substitutions
(as in mono- and polyalphabetic substitution ciphers)
and
transpositions
(as in columnar transposition ciphers). It turns out that digital counterparts to these exist and
are widely used in modern cryptography.
4.3.1 S-Box
The terminology for a digital substitution is called a
substitution box
,or
S-box.
The term
box
comes from the
fact that it is regarded as a simple function: It merely accepts some small input and gives the resulting output,
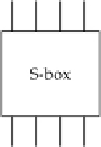
using some simple function or lookup table. When shown graphically, S-boxes are drawn as simple boxes, as in
Figure 4-1
Graphical representation of a 4-bit S-box.
S-boxes normally are associated with a
size,
referring to their input and output sizes (which are usually the
same, although they can be different). For example, here is a representation of a 3-bit S-box, called simply S:
S[0] = 7 S[3] = 4 S[6] = 0
S[1] = 6 S[4] = 3 S[7] = 1
S[2] = 5 S[5] = 2
This demonstrates one of the simpler methods of showing an S-box: merely listing the output for every input.
As we can see, this S-box,
S,
almost reverses the numbers (so that 0 outputs 7, 1 outputs 6, etc.), except the last
two entries for S[6] and S[7].
We can also specify this S-box by merely writing the outputs only: We assume that the inputs are implicitly
numbered between 0 and 7 (since 7 = 2
3
- 1). In general, they will be numbered between 0 and 2
b
- 1, where
b
is the input bit size. Using this implicit notation, we have
S
written as
[7, 6, 5, 4, 3, 2, 0, 1]
Search WWH ::

Custom Search