Cryptography Reference
In-Depth Information
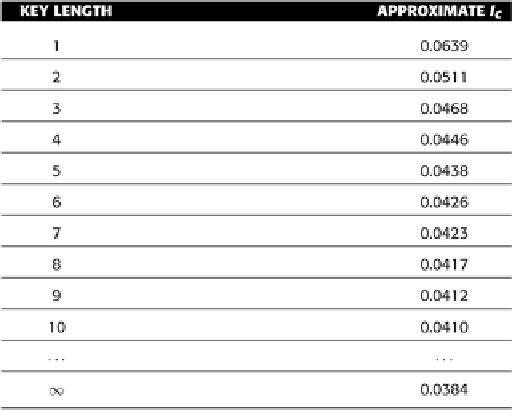
As can be seen, the measurement starts to get pretty fuzzy with key lengths of around six or so characters.
Without a great deal of ciphertext, it becomes very difficult to tell the difference between a polyalphabetic key
length of six and seven, even.
We clearly cannot rely completely on the
I
C
for determining the key length, especially for smaller amounts
of ciphertext (since it is only effective with large amounts of text, and not very precise for larger keys). Luckily,
we have another method for guessing at the likely key length.
Friedrich Kasiski discovered that there is another pattern that can be seen, similar to the index of coincidence
[4]. In English, for example,
the
is a very common word. We would, therefore, assume that it will be encrypted
multiple times in a given ciphertext. Given that we have a key length of
n
, we can hope that we will have the
word
the
encrypted at least
n
times in a given ciphertext. Given that it is encrypted at least that many times,
we will be guaranteed to have it be encrypted to the
exact same
ciphertext at least twice, since there are only
n
different positions that
the
can be aligned to with regard to the key.
We know that we can expect there to be repetitions of certain strings of characters of any common patterns
(any common trigraphs, e.g.). But what does this reveal about the key? This will actually give us several clues
about the length of the key.
If we are very certain that two repetitions of ciphertext represent the exact same plaintext being encrypted
with the same pieces of the key, and we know that the key is repeated (such as in Vigenère) over and over again,
this means that it must be repeated over and over again in between those two pieces of ciphertext. Furthermore,
it means that they were repeated an integral number of times (so that it was repeated 15 or 16 times, but not
14.5). Therefore, we calculate the difference in the positions of the two pieces of ciphertext, and we know that
this
must
be a multiple of the length of the ciphertext. Given several of these repetitions, and several known
multiples of the length of the cipher key, we can start to hone in on the exact length of the key.
A good example may help clear up what is going on. The following plaintext is from the prologue to
Romeo
and Juliet
[3]:
twoho useho ldsbo thali keind ignit yinfa irver
onawh erewe layou rscen efrom ancie ntgru dgebr
eakto newmu tinyw herec ivilb loodm akesc ivilh
andsu nclea nfrom forth thefa tallo insof these
twofo esapa irofs tarcr ossdl overs taket heirl
Search WWH ::

Custom Search