Cryptography Reference
In-Depth Information
allows the use of encryption techniques similar to the ones we have used in English so far, showing some dif-
ferent properties of the language.
Table 1-2
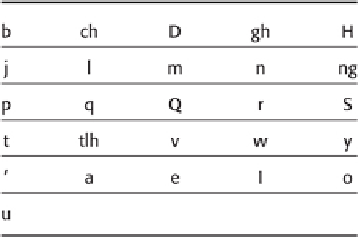
shows all of the characters of tlhIngan Hol as they are commonly spelled in the Latin alphabet.
From this table, we can then determine that the 25 characters,
abcDeghHIjlmnopqQrStuvwy'
, are the
only ones we should be seeing and therefore need to encrypt (note that English has 52 characters, if you include
capital letters).
Table 1-2
Sounds of tlhIngan Hol [1]
Using the character ordering of the previous paragraph, we can perform a ROT13 of the Klingon text:
Heghlu'meH QaQ jajvam
(In English, this translates as “Today is a good day to die.”)
After the ROT13, we obtain the enciphered text:
trStyln'rt DoD wowjo'
1.3 Polyalphabetic Ciphers
We can naturally think of several ways to make the monoalphabetic cipher a more powerful encryption scheme
without increasing its complexity too much. For example, why not use two different ciphers, and switch off
every other letter? Or use three? Or more?
This would be an example of a
polyalphabetic cipher.
These began to be widely adopted over the past 500
years or so owing to the increasing awareness of how weak monoalphabetic ciphers truly are. There are a few
difficulties in managing the alphabets. A key must be used to select different alphabets to encrypt the plaintext.
However, this necessitates an increase in key complexity. If a key represents some set of
k
alphabets, then
there are (26!)
k
different sets of alphabets that could be chosen. (This is 26 factorial to the
k
-th power. In other
words, take the number 26 and multiply it by 25, 24, and so on down to 2, and take
that
number, and multiply it
by itself
k
times. With
k
= 1, this is about four hundred million billion billion, or a 4 followed by 23 zeros. The
number of zeros roughly doubles with each increment of
k
.) To reduce this number, cryptographers often use a
small number of alphabets based on easily remembered constructions (such as shifts and reversals of the normal
alphabetic ordering), and use parts of the key to select alphabets used for substitution.
Search WWH ::

Custom Search