Cryptography Reference
In-Depth Information
lowing the same rule. Since these rules must always translate a character in the same way every time, a rule can
be represented as a new alphabet, so that a message can be encrypted via a conversion table between the two
alphabets.
Thesimplestexampleofamonoalphabeticcipheristoperformasingleshiftonthealphabets.Inotherwords,
replace all
a'
s with
b'
s,
b'
s with
c'
s, and so forth, and wrap around the end so that
z'
s are replaced with
a'
s. This means that the word cat would be encrypted as
DBU
, and the word
EPH
would be decrypted as
dog
.
One of the first, and certainly the most widely known, monoalphabetic ciphers was one used by ancient Ro-
mans. It is affectionately called the
Caesar cipher
after the most famous of Romans [4]. This system was re-
portedly used to encrypt battle orders at a time when having the orders written at all was almost good enough
to hide them from the average soldier, and it is extraordinarily simple. To obtain the ciphertext for a plaintext
using the Caesar cipher, it is necessary simply to exchange each character in the plaintext with the correspond-
ing character that occurs three characters later in the common order of the alphabet (so that a encrypts to
D, b
encrypts to
E
, etc., and wrapping around, so that
x
encrypts to
A
).
Naturally, getting the plaintext back from the ciphertext is simply a matter of taking each character and repla-
cing it with the character that appears three characters before it in the common order of the alphabet (see
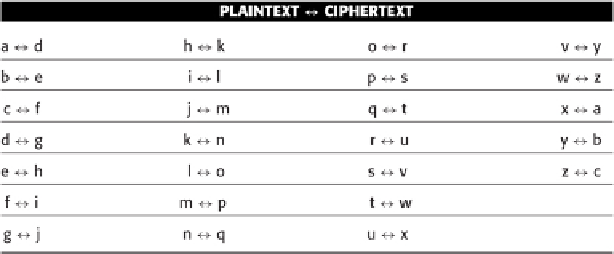
Table
Table 1-1
Caesar Cipher Lookup Table
For example, the text
retreat
would be encoded as
UHWUHDW
.
To decrypt a message, simply reverse the table so that d
⇒
a, e
⇒
b, and so on.
As a quick example, the text
the quick brown roman fox jumped over the lazy ostrogoth dog
can be easily encrypted by shifting each character three to the right to obtain
WKH TXLFN EURZQ URPDQ IRA MXPSHG RYHU WKH ODCB RVWURJRWK GRJ
However, as any person experienced in newspaper crypto-puzzles can tell you, one of the key features to
breaking these codes is found in the placement of the spaces: If we know how many letters are in each word, it
will help us significantly in guessing and figuring out what the original message is. This is one simple cryptana-
lytic piece of knowledge we can use right away — we are not encrypting the spaces! There are two solutions:
We can either encrypt the spaces as an additional “27-th” letter, which isn't a terrible idea, or remove spaces
altogether. It turns out that it makes slightly more sense, cryptanalytically speaking, to remove the spaces alto-
gether. This does make it hard to read and write these codes by hand; thus, we often just remove the spaces but
add in new ones at regular intervals (say, every four or five characters), giving us ciphertext such as
Search WWH ::

Custom Search