Cryptography Reference
In-Depth Information
Note that the
E
1
-1
characteristic works from the ciphertext to the intermediate ciphertext (outside inwards). The
differentials are used in the following relations:
Using these two characteristics, we can then derive a new characteristic for the intermediate encryption of
Q
0
and
Q
1
:
Hence, we have derived a new characteristic for the
Q
values:
This characteristic can then be measured by calculating
Q
0
⊕
Q
1
= Ω.
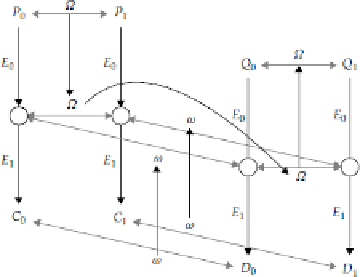
Figure 7-3
shows a graphical repres-
entation of how this characteristic occurs.
Figure 7-3
Derivation of the boomerang differential
P
0
⊕
P
1
= Ω leading to
Q
0
⊕
Q
1
= Ω based on a diagram
in Reference [20]. (Light gray lines) XOR's; (dark gray lines) how the differentials propagate from the
P
's to
the
Q
's; (black lines) encryption.
From the diagram and the derivation above, we can see why this is called the
boomerang attack:
If we con-
struct the differentials correctly, the differential Ω will come back and hit us in
Q
0
⊕
Q
1
.
We construct the boomerang differential by taking a seed plaintext
P
0
with our Ω differential and creating
P
1
=
P
0
⊕
Ω. We then encrypt
P
0
and
P
1
to obtain
C
0
and
C
1
, respectively. Next, we calculate new ciphertexts
with our ω differential, so that
D
0
=
C
0
⊕
ω and
D
1
=
C
1
⊕
ω. We then decrypt
D
0
and
D
1
to obtain
Q
0
and
Q
1
.
Some percentage of the time, the moons will align and the differentials will all line up, allowing us to measure
to see if
Q
0
⊕
Q
1
= Ω. When all four differentials hold, we refer to this as a
right quartet
.
What is the significance of this attack? Well, many algorithms have been deemed to be “secure” against dif-
ferential cryptanalysis because of the lack of any good characteristics on the full cipher. Normally, as the num-
ber of rounds increases, the probability of the differential decreases, thereby requiring more and more plain-
text-ciphertext pairs.
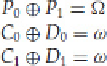

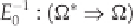
Search WWH ::

Custom Search