Cryptography Reference
In-Depth Information
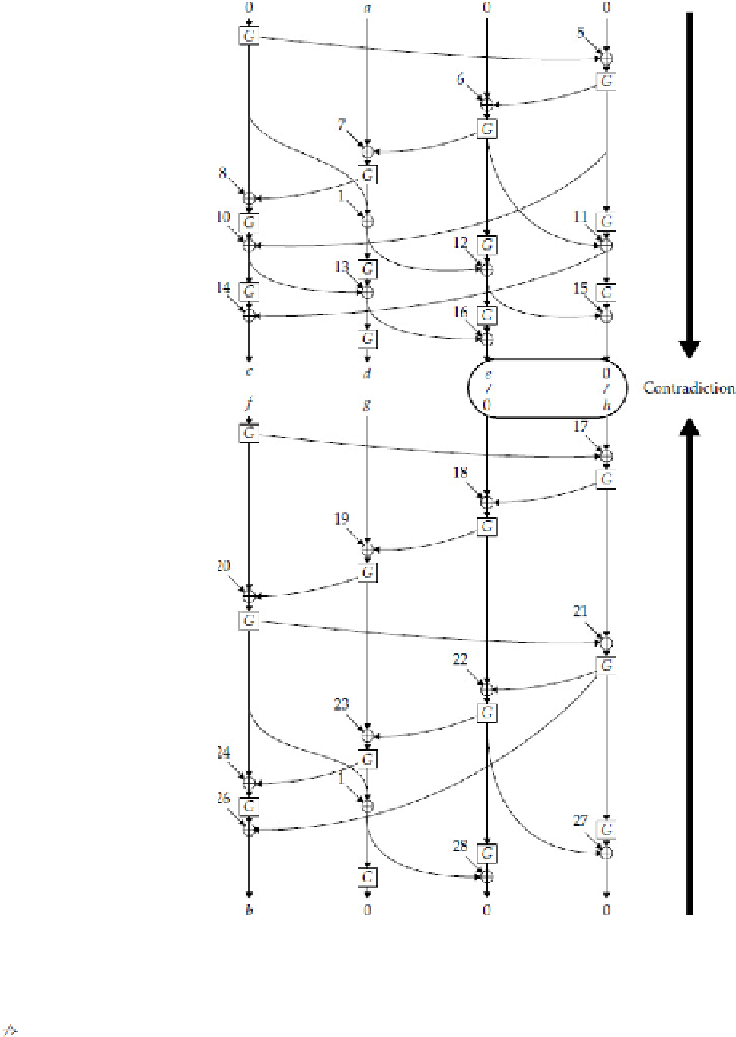
Figure 7-2
A graphical depiction of the impossible differential attack on Skipjack, based on a diagram from
Reference [4]. The rounds have been “unrolled” from the shift register mechanism, allowing us to more easily
see the mechanism. We can see the differentials missing in the zero, as one side predicts a zero, and the other
side predicts a non-zero intermediate.
For the exact details of the full attack, including complete details on a key recovery attack, see Reference [4].
However, I'll outline the attack below.
This technique can be used to derive a key in the following way. We use the above differential [(0,
a
, 0, 0)
(
b,
0, 0, 0) ] to ferret out all of the invalid subkeys. We launch an attack very similar to a standard differen-
tial attack, where we expect to predict the key by using the plaintext-ciphertext to test a differential as above.
Search WWH ::

Custom Search