Cryptography Reference
In-Depth Information
The fundamental concept here is that of
measured differences in values
. We use the term
differential
to
mean the XOR difference between two particular values, that is, the XOR of the two values. Differentials are
often denoted as
Ω
values, such as Ω
A
and Ω
B
.
A
characteristic
is composed of two differentials, say Ω
A
and Ω
B
, written as
The idea is that a characteristic is showing that the differential, Ω
A
, in an input gives rise to another differential,
Ω
B
, in an output. Most of the time, this characteristic is not a certainty; it will be true only some of the time.
Hence, we are often concerned with the
probability
that a differential Ω
A
in the input will result in a differential
Ω
B
in the output.
As a quick example, assume that we are using a simple XOR cipher that encrypts data by XORing each byte
with an 8-bit key (which is the same throughout). Hence, a message representing the text
"hello"
in hexa-
decimal ASCII would be
68 65 6c 6c 6f
If we XORed this with the constant hex key
47
, we would get
2f 22 2b 2b 28
We can try to use a differential of, say,
ff
(all ones) in the original plaintext, and then XOR again with the
key to obtain a new ciphertext:
d0 dd d4 d4 d7
Finally, we compare the two ciphertexts by XORing them, obtaining the differential:
ff ff ff ff ff
Note that this is the exact differential we used on the plaintext! This should give us a clue that the cipher is
not very strong. We can then write the characteristic for this as
(ffffffffff
⇒
ffffffffff)
We consider input and output here to refer to either the input and output of a S-box, some number of rounds
of a cipher, or the total cipher itself. Most importantly, we will take characteristics of an S-box to create char-
acteristics for various rounds, which are then stitched together to create a characteristic for the entire cipher —
this is how a standard differential attack is realized.
7.3 S-Box Differentials
Now we are ready to start analyzing the components of a cipher. Since most ciphers utilize S-boxes (or
something analogous, such as the
SubBytes
operation in AES) at their heart, it is natural to start there. Thus, the
first step of differential cryptanalysis is to compute the characteristics of inputs and the outputs of the S-boxes,
which we will then stitch together to form a characteristic for the complete cipher.
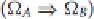
Search WWH ::

Custom Search