Cryptography Reference
In-Depth Information
The values with the prime (′) indicate the new values to be assigned.
After the 64 steps are completed, the new values for
a, b, c,
and
d,
are added into the working hash buffer (
A
,
B
,
C
,
D
). Then, the next block is loaded, and the process is run again.
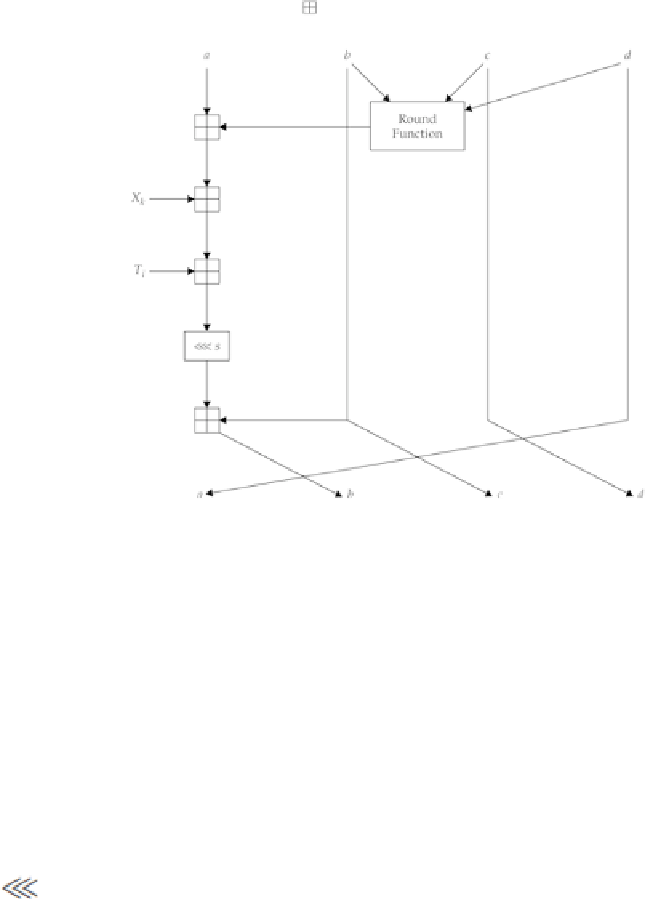
See
Figure 4-21
for a graphical representation of this.
Figure 4-21
Basic round of MD5. Here, the “ ” operator represents arithmetic addition, modulo 2
32
(i.e.,
32-bit addition).
Finally, the new values are arithmetically added back into the old values (with 32-bit arithmetic):
When the last block is processed, the MD5 signature is the final value of (
A, B, C, D)
.
4.12.4 SHA-1
The
Secure Hash Algorithm 1 (SHA-1)
[10] is a hashing algorithm specified by NIST that outputs a 160-bit
hash.
The following description is based on References [16] and [18].
SHA-1 takes the input as 512-bit blocks and further splits them into 16 32-bit words, labeled
m
0
through
m
15
.
The words are expanded into 80 such words by the following equation, for
i = 16, ... , 79:
where the 1 operation rotates the bits, circularly, left by 1.
The initial values of (
a
0
,
b
0
,
c
0
,
d
0
,
e
0
) and
(A, B, C, D, E)
are
(67452301, efcdab89, 98badcfe, 10325476, c3d2e1f0)
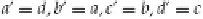


Search WWH ::

Custom Search