Cryptography Reference
In-Depth Information
4.10.5 Counter Mode
Ciphers can also be operated in
counter (CTR) mode
, which can also be used to convert them to a stream
cipher [3].
A series of counters is used, say,
C
0
,
C
1
, and so on. These counters are normally just increments of one an-
other, hence the term
counter
. The first counter,
C
0
, should normally be a number that is difficult to guess.
The ciphertext for a given set of plaintext bits is then obtained as follows:
1. Encrypt the next counter with the key.
2. Extract the number of bits required, using the most significant bits first. At least one bit will be extrac-
ted, and up to all of the bits can be.
3. XOR the selected bits with the plaintext bits.
The result of the last step is then the ciphertext bits. For the next batch of plaintext bits, encrypt the next counter,
and so forth.
4.11 Skipjack
Skipjack
[17] is a combination of many different cipher techniques, including large permutations and shift re-
gisters. It is a very unique block cipher that operates on 64-bit blocks. It uses an unbalanced Feistel network and
an 80-bit key.
Skipjack was designed by the U.S. Government to provide a robust encryption algorithm that enabled law
enforcement to decrypt messages through an escrowed key. In other words, the algorithm is designed so that a
copy of the key is encoded in such a way that law enforcement could, with an appropriate court order, obtain
the key. However, the law enforcement and key escrow portions are not what we are mostly concerned about,
but the inner workings of the encryption algorithm itself.
Skipjack is a very unique algorithm, differing in many ways from the traditional Feistel structures and SPNs
studied above. For example, many of its operations are in the form of shift registers, rather than straight Feistel
or SPN structures, although some of the functions used in the shift registers employ these techniques.
4.11.1 Skipjack Encryption Algorithm
Skipjack's encryption algorithm works fairly simply. There are two rules used in different rounds for a total of
32 rounds.
The plaintext is split into four parts (each being a 16-bit value):
and . For each round, the plain-
text is either executed through a loop of Rule A or Rule B.
Both rules rely on a permutation, usually written as
G
. The exact nature of
G
depends on the round
k
(since
the key mixing is done in the
G
permutation), so it can also be written as
G
k
.
Skipjack Rule A
Rule A follows a simple cyclical structure. Note that the counter is incremented every round.
1. Set the new
w
1
value to be the
G
permutation of the old
w
1
, XORed with the old
w
4
value, as well as
the counter.
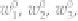

Search WWH ::

Custom Search