Cryptography Reference
In-Depth Information
ous block (with the first block dependent also on the initialization vector).
Figure 4-16
shows how this elimin-
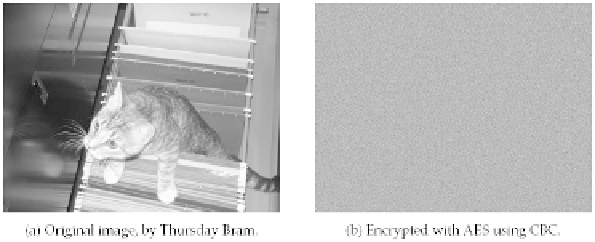
ates block replay attacks by ensuring that the same plaintext blocks will be encrypted differently.
Figure 4-16
A picture of a cat in a filing cabinet. Unlike ECB, CBC obliterates much of the underlying struc-
ture.
CBC Encryption
The following describes the basic CBC method, as described in Reference [9]. The method uses a 64-bit block
size for plaintext, ciphertext, and the initialization vector (since the reference originally assumes that DES is
used, although any cipher can be used in CBC mode). To adapt it for other ciphers, simply change this to the
relevant block size, and use the appropriate algorithm.
1. Calculate the first block to send by taking the IV and the first block of plaintext, XORing them, and
encrypt the result. Hence,
C
0
=
Encrypt
(
P
0
⊕
IV
)
2.CalculateeachsuccessiveblockbyXORingthepreviousciphertextblockwiththenextplaintextblock,
and encrypting the result. Hence, for
i
≥ 1,
C
i
=
Encrypt
(
P
i
⊕
C
i
-1
)
Decryption in CBC is equally simple.
CBC Decryption
The biggest restriction is that the two users must share the IV or the first block will not be comprehensible to
the receiver.
1. Decrypt the first received ciphertext block, and XOR the result with the IV to obtain the first plaintext.
Hence,
P
0
=
IV
⊕
Decrypt
(
C
0
)
2. For each successive received block, take the received block of ciphertext, run it through decryption,
and then XOR it with the previous round's
ciphertext
to obtain the next plaintext. Hence, for
i
≥ 1,
P
i
=
C
i
-1
⊕
Decrypt
(
C
i
)
Search WWH ::

Custom Search