Cryptography Reference
In-Depth Information
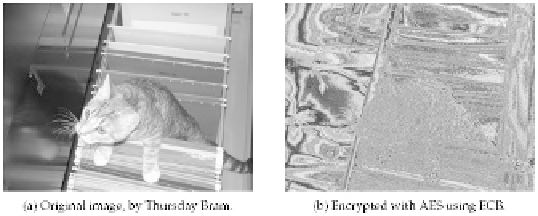
Figure 4-15
A picture of a cat in a filing cabinet, demonstrating the preserved structure present in ECB.
Ingeneral, when identical plaintext blocks always encrypt to identical ciphertext blocks, there is the potential
for a problem with
block replay
: Knowing an important plaintext-ciphertext pair, even without knowing the
key, someone can repeatedly send the known ciphertext.
For example, assume that we have a very simple automatic teller machine (ATM), which communicates with
a bank to verify if a particular individual is authorized to withdraw cash. We would hope that, at the very least,
this communication between the ATM and the bank is encrypted. We might naively implement the above scen-
ario in a simple message from the ATM:
ATM:
Encrypt
K
(“Name: John Smith, Account: 12345, Amount: $20”)
(Assume that the bank sends back a message saying, “OK, funds withdrawn,” or “Sorry, insufficient funds.”)
The above means simply to send the text message, encrypted with the key
K.
If the encryption scheme merely
represented this as an ASCII message and performed an algorithm, such as AES, using the key
K,
we might
think we are safe, since anyone listening in on the transaction will only see something random, such as
ATM: CF A2 1E C5 AF 67 2D AC 7A E1 0D 3B 2F ...
However, someone could do something sinister even with this. For example, someone listening in on this
conversation might simply want to replay the above packet, sending it to the bank. Unless additional security
measures are in place, the bank will think that the user is making several more ATM withdrawals, which could
eventually drain the victim's bank account.
Even though the ATM used strong encryption to communicate with the bank, it was still susceptible to a
block replay attack. Luckily, there are methods to help prevent this attack.
4.10.2 Cipher Block Chaining
One of the most fundamental ideas of combatting the block replay problem is to make the output of each block
dependonthevaluesofthepreviousblocks.Thiswillmakeitsothatanyonelisteningtoanyblockinthemiddle
will not be able to repeat that one block over and over again at a later date.
However, simply chaining together the outputs like this still leaves a flaw: It does not prevent block replay
of
the first
block (or the first several blocks, if they are all replayed). A common strategy to fight this is to add
an
initialization vector
(the IV, and sometimes called the “salt”) to the algorithm. Essentially, this is a random
number that is combined with the first block, usually by XORing them together. The IV must also be specified
somehow, by sending it to the other party or having a common scheme for picking them.
Using both of these strategies together results in the simple method called
cipher-block chaining (CBC)
.
The method I will describe is taken from Reference [9]. It essentially makes each block dependent on the previ-
Search WWH ::

Custom Search