Cryptography Reference
In-Depth Information
where the
a
i,c
entries on the right are the old column entries, the
b
i,c
entries on the left are new column entries,
and the
⊗
operator means to perform matrix multiplication with the • operator and XOR instead of addition. We
can specify this less abstractly as
This operation will be performed for each column, that is, for
c
= 1, 2, 3, and 4.
The
MixColumns
operation is shown graphically in
Figure 4-13
.
Figure 4-13
The Rijndael
MixColumns
operation.
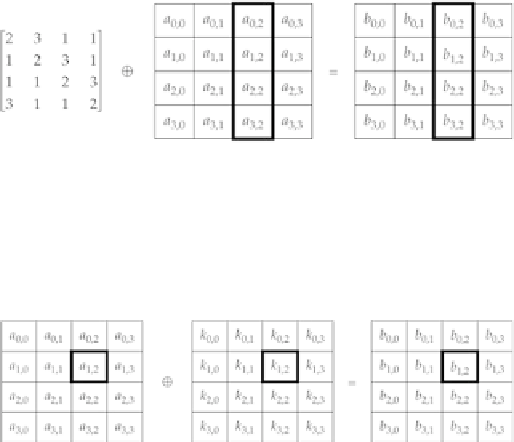
4.9.1.4 AddRoundKey
Finally, the
AddRoundKey
operation takes each 8-bit value of the state and XORs it with an 8-bit value of the
key schedule, as shown in
Figure 4-14
.
Figure 4-14
The Rijndael
AddRoundKey
operation.
4.9.2 Rijndael Decryption Algorithm
Decryption of Rijndael is very similar to encryption: It simply involves doing the operations in reverse (with
a reverse key schedule) and using inverse operations for
SubBytes, MixColumns,
and
ShiftRows
—these opera-
tions are called, surprisingly enough,
InvSubBytes, InvMixColumns,
and
InvShiftRows,
respectively.
The use of these inverse functions leads to the following algorithm for decryption:
Rijndael Decryption Algorithm
Assume that there are
r
rounds (
r
is dependent on the key size) and that the ciphertext is loaded into the state.
1. Run
AddRoundKey
on the state.

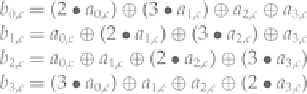
Search WWH ::

Custom Search