Cryptography Reference
In-Depth Information
Rijndael Encryption Algorithm
Assume that there are
r
rounds (
r
is dependent on the key size), and that the plaintext has been loaded into the
state.
1. Run
AddRoundKey
on the state.
2. Do the following
r
− 1 times.
(a) Run
SubBytes
on the state.
(b) Run
ShiftRows
on the state.
(c) Run
MixColumns
on the state.
(d) Run
AddRoundKey
on the state.
3. Run
SubBytes
on the state.
4. Run
ShiftRows
on the state.
5. Run
AddRoundKey
on the state.
I'll now describe the four sections in a bit more detail. For a more thorough treatment, see References [2]
and [7]. The following examples use the details in the AES for a 128-bit block size.
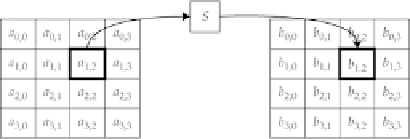
4.9.1.1 SubBytes
The
SubBytes
operation essentially functions as an 8-bit S-box, applied to each 8-bit value of the state, as shown
in
Figure 4-11
.
Figure 4-11
The Rijndael
SubBytes
operation.
The S-box can be represented in several ways. The normal S-box implementation, with a fixed lookup table,
is shown in
Figure 4-2
.
The way I often show it is, if I define the 8-bit input
a
to be written as
a
7
||
a
6
|| ... ||
a
0
and
b
to be written similarly, then
where the × operator means matrix multiplication. If this is confusing, it is fairly easy, and often faster, to
just use the lookup-table representation of the S-box.

Search WWH ::

Custom Search