Cryptography Reference
In-Depth Information
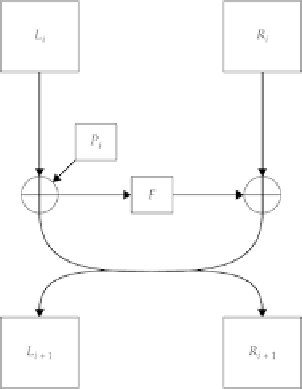
Figure 4-9
The Blowfish algorithm's main encryption loop.
4.8.3 Blowfish Round Function
The core of the algorithm is, as with all Feistel structures, in the round function.
Blowfish Round Function
In this case, the round function
(f
in the algorithm) works on a 32-bit argument and produces a 32-bit output by
the following method:
1. Divide the 32-bit argument into four 8-bit values:
a, b, c,
and
d.
2. Using unsigned arithmetic, calculate
S
1,
a
+
S
2,
b
. Take the result as a 32-bit integer (ignoring any portion
that might have extended beyond 32 bits).
3. Calculate the XOR of the result of Step 2 and the output of
S
3,
c
.
4. Finally, take the result of Step 3 and add (unsigned, with 32-bit arithmetic, as before)
S
4,
d
. This will be
the result of the round function.
4.8.4 Notes on Blowfish
This round function has a few interesting properties. Notably, which S-boxes are chosen depends on the data
themselves: so that the data dictate their own encryption. [This is because the split plaintext
(a, b, c,
and
d)
is
used to choose the S-boxes.]
The other important note about Blowfish is that it requires 521 encryptions using its own encryption al-
gorithm before it can produce a single block of output. Therefore, encrypting a single block would take very
long because of the long setup time. It really only becomes moderately fast to use Blowfish when encrypting
at least several hundred blocks (meaning thousands of bits); otherwise, the setup time will dominate the total
encryption and decryption times. Luckily, we need to compute the key values and S-boxes only once.
Search WWH ::

Custom Search