Cryptography Reference
In-Depth Information
01, 02, 04, 08, 10, 20, 40, 80, 1b, 36, 6c, d8, ab, 4d, 9a, 2f, 5e, bc, 63, c6, 97, 35, 6a,
d4, b3, 7d, fa, ef, c5, 91, 39, 72, e4, d3, bd, 61, c2, 9f, 25, 4a, 94, 33, 66, cc, 83, 1d,
3a, 74, e8, cb, 8d
After the 51
st
iteration, it wraps back around to 0x01 and starts repeating.
This strange-looking formulation enables you to produce unique values sim-
ply and quickly for quite a while, although the key schedule computation only
requires 10 iterations (this comes up again in the
column mixing
in the actual
encryption/decryption process). Of course, you could have just added one each
time and produced 255 unique values, but the bit distribution wouldn't have
been as diverse. Remember that you're XORing each time; you want widely
differing bit values when you do this.
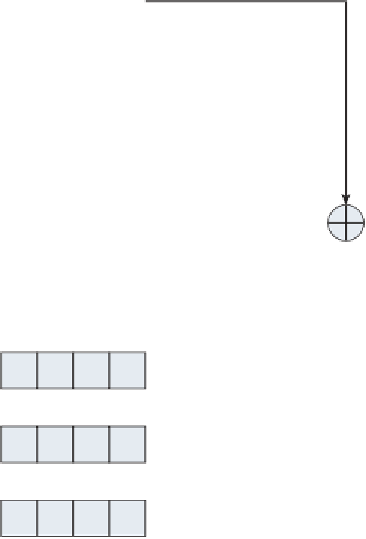
So, for a 128-bit key, the actual key schedule process looks more like what's
shown in Figure 2-10.
Initial Key Input
Key Schedule
bytes 1-4
bytes 5-8
bytes 9-12
bytes 13-16
bytes 17-20 =
sub (rot (bytes
1-4 xor bytes
13-16) )
Sub
Sub
Sub
Sub
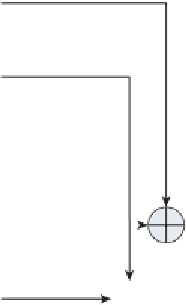
bytes 21-24 =
bytes 5-8 xor
bytes 17-20
bytes 25-28 =
bytes 9-12 xor
bytes 21-24
bytes 29-32 =
bytes 13-16 xor
bytes 25-28
bytes 33-36 =
sub (rot (bytes
17-20 xor
bytes 29-32) )
Sub
Sub
Sub
Sub
Figure 2-10:
AES 128-bit key schedule computation

























Search WWH ::

Custom Search