Cryptography Reference
In-Depth Information
8
7
6
5
4
3
2
1
1
2345678
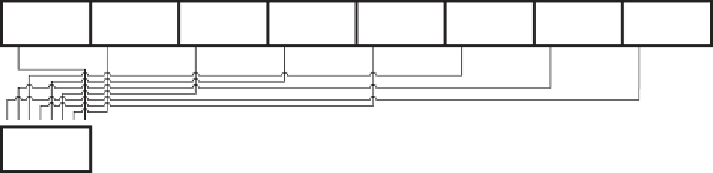
Figure 2-2:
First byte of output
8
7
6
5
4
3
2
1
1
2345678
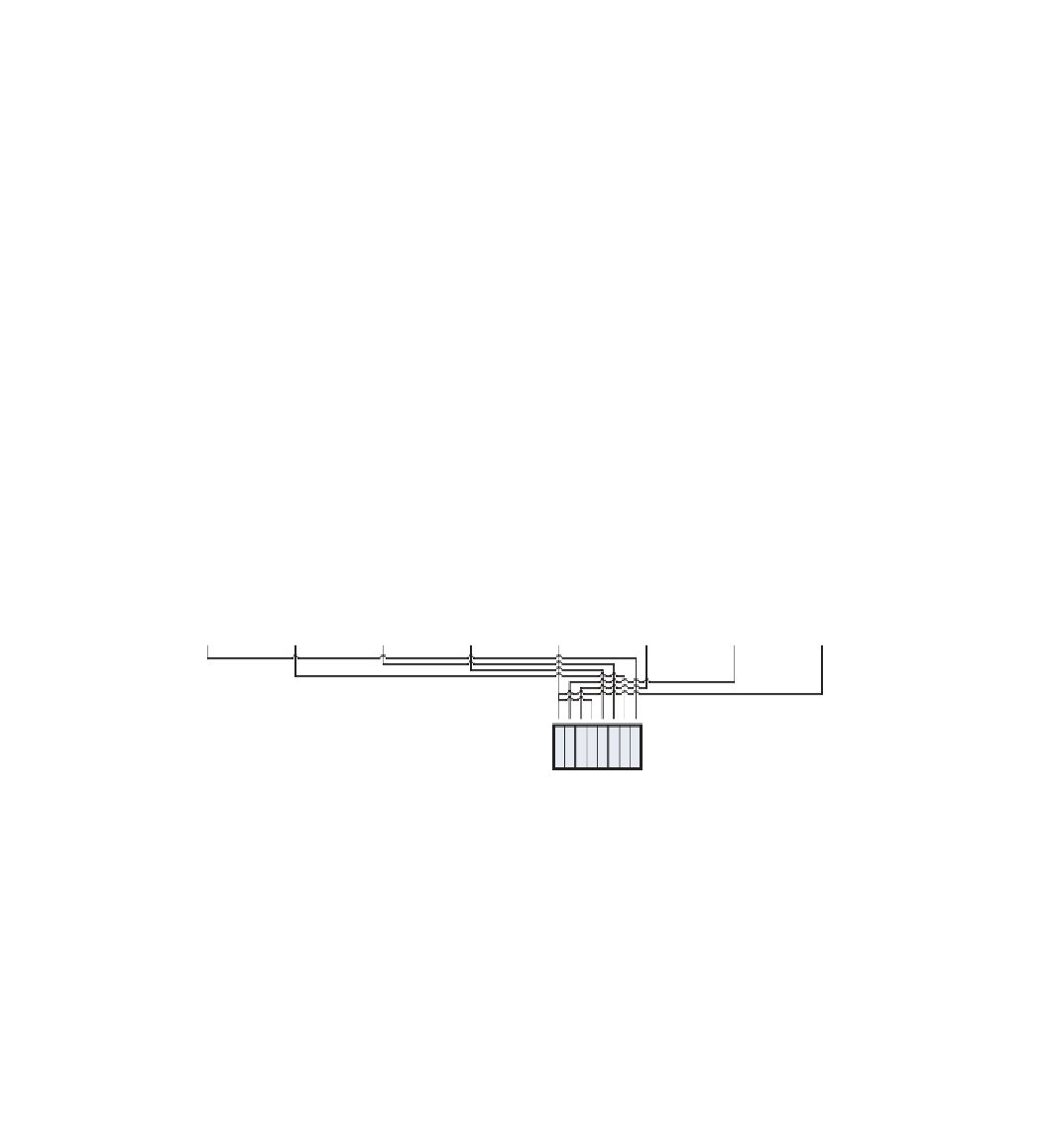
Figure 2-3:
Second byte of output
and so on for bytes 3 and 4; the fi fth byte of output comes from the fi rst bit of
input as shown in Figure 2-4:
8
7
6
5
4
3
2
1
1
2345678
Figure 2-4:
Five permuted bytes
and so on until all of the input bits were exhausted.
You can code this all in a very terse loop without using a lookup table on that
basis, something like what's shown in Listing 2-4.
Listing 2-4:
Terse initial permutation
for ( i = 1; i != 8; i = ( i + 2 ) % 9 )
{
for ( j = 7; j >= 0; j-- )
(Continued)























































Search WWH ::

Custom Search