Cryptography Reference
In-Depth Information
}
memcpy( padded_block + hash_block_length, hash1,
hash_code_length * sizeof( int ) );
digest_hash( padded_block,
hash_block_length + ( hash_code_length * sizeof( int ) ), hash_out,
hash_code_length, hash_block_operate, hash_block_finalize );
free( hash1 );
free( ipad );
free( opad );
free( padded_block );
}
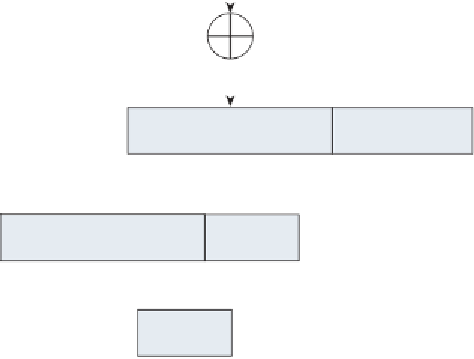
Key
0
×
36 0
×
36 0
×
36 ...
text
hash (e.g. MD5 or SHA-1)
0
×
5c 0
×
5c 0
×
5c
hash code
hash
HMAC
Figure 4-1:
HMAC Function
The method signature is a behemoth, repeated in Listing 4-20.
Listing 4-20:
“hmac.h” HMAC function prototype
void hmac( const unsigned char *key,
int key_length,
const unsigned char *text,
int text_length,
int (*hash_block_operate)(const unsigned char *input, unsigned int hash[] ),
int (*hash_block_finalize)(unsigned char *block, int length ),
int hash_block_length,
int hash_code_length,
unsigned int *hash_out )











Search WWH ::

Custom Search