Cryptography Reference
In-Depth Information
Listing 3-4:
“huge.c” add routine (addition loop)
i = h1->size;
j = h2->size;
do
{
i--;
if ( j )
{
j--;
sum = h1->rep[ i ] + h2->rep[ j ] + carry;
}
else
{
sum = h1->rep[ i ] + carry;
}
carry = sum > 0xFF;
h1->rep[ i ] = sum;
}
while ( i );
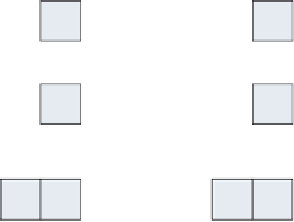
Most signifi cantly, start at the end of each array, which, again, could be two
different sizes, although
h2
is guaranteed to be equal to or smaller in length
than
h1
. Each
char
can be added independently, working right-to-left, keeping
track of overfl ow at each step, and propagating it backward to the subsequent
char
, as shown in fi gure 3-2.
i
=
4
i
=
5
j
=
4
j
=
5
h1->rep
x
x
x
x
x
x
h2->rep
x
x
x
x
x
+
x
+
x
x
sum
x
x
sum
carry
carry
Figure 3-2:
Large number addition
Note that the overfl ow cannot be more than one bit. To convince yourself that
this is true, consider adding two four-bit numbers. The largest such (unsigned)
number is 15 ( bi nary 1111). If you add 15 and 15, you get:






















Search WWH ::

Custom Search