Cryptography Reference
In-Depth Information
1
st
16 bytes of key
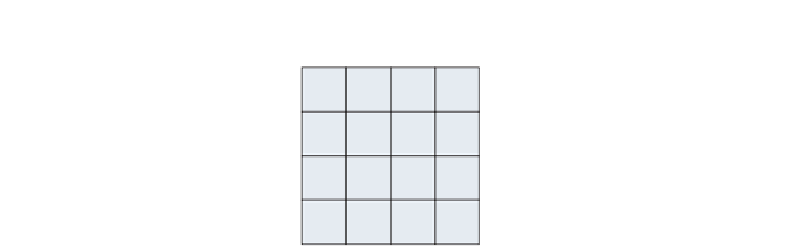
Input Block (“State”)
Round #1 Input
Figure 2-12:
AES key combination
Listing 2-33:
“aes.c” add_round_key
static void add_round_key( unsigned char state[ ][ 4 ],
unsigned char w[ ][ 4 ] )
{
int c, r;
for ( c = 0; c < 4; c++ )
{
for ( r = 0; r < 4; r++ )
{
state[ r ][ c ] = state[ r ][ c ] ^ w[ c ][ r ];
}
}
}
Note that this is done before the rounds begin.
Each round consists of four steps: a substitution step, a
row-shifting
step, a
column-mixing
step, and fi nally a key combination step.
Substitution is performed on each byte individually and comes from the same
table that the key schedule substitution came from, as in Listing 2-34.









Search WWH ::

Custom Search