Information Technology Reference
In-Depth Information
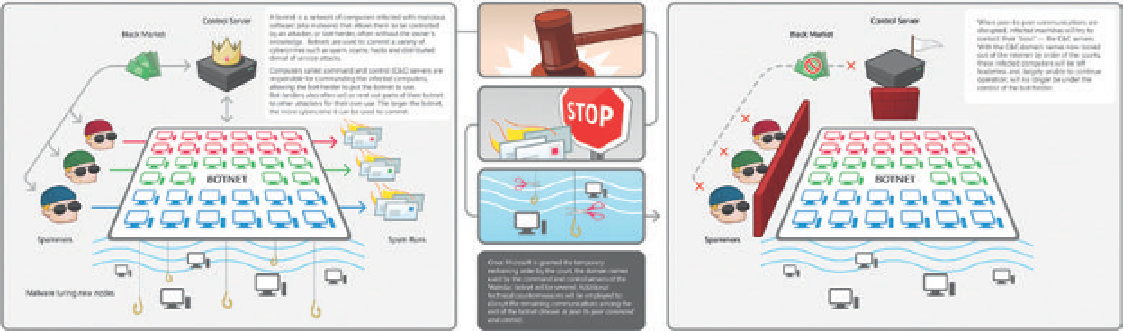
Fig. 12.7. Nefarious botnet programs
work by hijacking millions of comput-
ers, usually without their owners'
knowledge.
Botnets and zombie computers
The last decade has seen a dramatic rise of hacking for profit by criminal
organizations.
Botnets
are collections of computers that have been taken over
by techniques such as those described above and are controlled by so-called
bot-herders
(see
Fig. 12.7
).
Bot
is short for
robot program
, and sometimes these
enslaved computers are known as
zombie computers
. The botnets can be used to
conduct
denial of service attacks
on specific websites (see
Fig. 12.8
) - such attacks
try to shut down a site by bombarding it with so many requests that the system
is forced to shut down, denying service to legitimate users. Botnets can also
be used to send spam or to capture personal details by
key logging -
capturing a
user's keystrokes. A recent example is the Conficker botnet that first appeared
in 2008. It was estimated to have infected more than ten million computers
around the world and to have the capacity to send an incredible ten billion
spam emails per day. Mark Bowden's topic,
Worm
, details how the white hat
security community collaborated with Microsoft to contain and partially elim-
inate the threat to the Internet posed by Conficker. However, a 2012 Microsoft
report states that
… the Conficker worm was detected approximately 220 million times
worldwide in the past two and a half years, making it one of the biggest
ongoing threats to enterprises. The study also revealed the worm continues
to spread because of weak or stolen passwords and vulnerabilities for which a
security update exists.
6
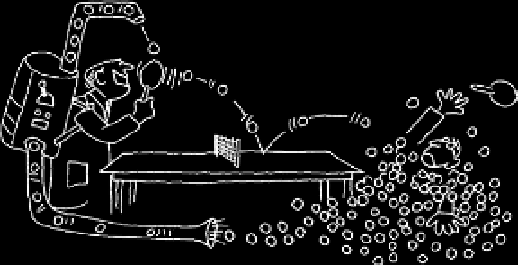
Fig. 12.8. This cartoon with the original
caption “… filibustering destroys com-
munication” captures the essence of a
“denial of service” attack.
Search WWH ::

Custom Search