Database Reference
In-Depth Information
Authorization in action
Now that we know how to create user accounts and grant and revoke permissions to them,
let's see how a non-superuser account behaves in practice. To do this, let's open up a new
cqlsh session logged in with our data analytics team's account:
$ cqlsh -u data_analytics -p verystrongpassword -k my_status
The
-k my_status
option simply tells cqlsh that we want to interact with the
my_status
keyspace, saving us the effort of issuing a
USE
statement.
Now let's see what we can do. First, we expect to be able to read data with no problem; let's
have a look at the
user_status_updates
table:
SELECT * FROM user_status_updates;
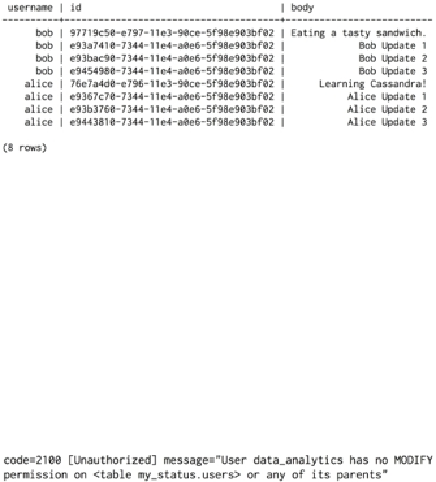
As expected, we have permission to read the contents of that table:
Now let's try making a change to some data. Though our analytics team certainly would
have no malicious intent, perhaps at some point the analytics cat may sit on a keyboard,
producing the following statement:
DELETE FROM "users"
WHERE "username" = 'alice';
That's quite an alarming query, but happily our authorization setup has saved us: