Information Technology Reference
In-Depth Information
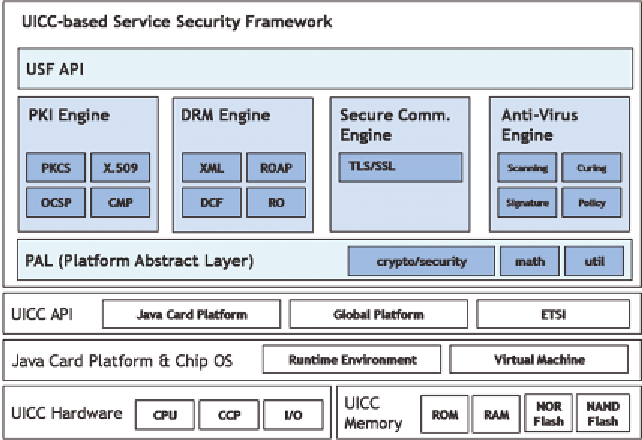
Figure 5. The Overall Architecture of UICC-based Service Security Framework (USF)
depending on the result of the verification. If the
EAP-AKA procedures are successful, then the
Authenticator and the mobile terminal (UICC)
can communicate each other securely using the
session key generated by the EAP-AKA.
Currently, the UICC-based network authentica-
tion service using the EAP-AKA is commercial-
ized in the Republic of Korea for WiFi, WiBro
and I-WLAN.
Nowadays, the UICCs which include much
more memories and enhanced performance are
introduced to the world and ready to be com-
mercialized in the near future. We would like to
explain a novel methodology to provide a secure
service infrastructure in the mobile terminal, the
UICC-based Service Security Framework (USF)
based on these enhanced UICCs.
We designed the USF as the core of security
infrastructure for the FMC environments to pro-
vide the integrated security infrastructure and
the security of the FMC services. The USF can
be utilized to authenticate users, preserve pri-
vacy and personal information, and protect the
network infrastructures and business models of
the telephony companies. The current version of
USF supports the security functionalities such as
PKI, DRM, TLS/SSL and Anti-Virus most likely
utilized in the FMC services.
We present the architecture of the USF. The
overall architecture of the USF is depicted in Figure
5. The USF mainly consists of three components;
USF APIs, USF Engines and PAL (stands for
Platform Abstract Layer).
UICC-Based Service
Security Framework
As explained earlier, the current UICCs are uti-
lized as simple information storages and calcula-
tors of crypto algorithms. However, the current
UICCs suffer from lack of memories utilized to
load and install the applets and don't implement
the PKI security functionalities such as RSA key
generation, some digital signature algorithms and
so forth, which can be utilized to extend the UICC
usages even though those APIs are defined in the
Java Card Platform standards due to the lack of
memories.
Search WWH ::

Custom Search