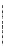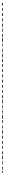Information Technology Reference
In-Depth Information
Fig. 2.
Structural View of GSA for “CSPF Confidential Data Transmission Using
Cryptographic Key-Based Symmetric Encryption”
! " !# #$
% ! &
% !&
% !#&
% !#&
#
#
% " #&
' (
' # #
% &
$ % &
#
#
Fig. 3.
Behavioral View Complementing Fig. 2
example a GSA for the machine domain of the CSPF confidential data trans-
mission using cryptographic key-based symmetric encryption. Figure 2 shows
the structural view of the GSA using a composite structure diagram. The
Sender
machine
domain loads the
Sent data
and
Cryptographic key
1
domains from a storage
device. Hence, we introduce the GNC
StorageManager
to access a storage device.
The
Sent data
domain is encrypted using the
Cryptographic key
1
domain. For this
reason, we introduce the GSC
SymmetricEncryptorDecryptor
presented in Sect. 3.2.
Furthermore, the
Sender machine
domain sends the encrypted data to the
Com-
munication medium
domain. Hence, we introduce the GNC
CommunicationManager
to access a network.
AccordingtotheCSPFthisGSAis related to, the plaintext
pt
represented in
the CSPF as lexical domain
Sent data
should be kept confidential. Hence, the GSC
SymmetricEncryptorDecryptor
and the GNC
Application
that makes use of this GSC