Information Technology Reference
In-Depth Information
Sign/Issue
Birth Certificate
Update
GBA Data
Send
Notifications
Close
Case
Receive Birth
Notification
Confirm
Identity
(GCD)
Search
GBA Data
Update
GBA Data
Receive Birth
Notification
Confirm
Identity
Search
GBA Data
Sign/Issue
Birth Certificate
Send
Notifications
Close
Case
(LCM)
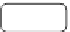
Fig. 6.
Synthesised GCD and LCM for the scenario of Fig. 1
Fig. 6 depicts the GCD for the variants of our initial example in Fig. 1. The
behavioural profile of the GCD comprises all constraints from model (
I
)asthey
are more restrictive than those imposed by model (
II
). The GCD visualises the
basic ordering constraints of both variants. Still, it is not identical to model (
I
)
as certain causalities are abstracted by the behavioural profile.
C2: Most general behaviour: Least Common Multiple.
The most general be-
haviour is referred to as the Least Common Multiple (LCM) of a set of variants.
It is characterised by a behavioural profile
B
LCM
over
A
that is derived by
computing the union of all profiles
B
P
n
. The LCM imposes solely the
weakest constraints for a pair of activities in the set of variants. Again, a model
is derived from
B
P
1
,...,
B
LCM
using the synthesis approach for behavioural profiles.
Fig. 6 depicts the LCM for the variants of our initial example. The parallel
execution of three activities is caused by the interleaving order imposed by the
profile of the LCM. As all of them may be executed multiple times (interleaving
order as a self-relation), they are also part of a control flow cycle. Note that
model synthesis for these activities includes various design decisions on how to
represent interleaving order (by concurrency or by cyclic structures) [26]. Hence,
the synthesis approach may be adapted so that an LCM with a different struc-
ture, but identical behavioural profile is created.
C3: Shared forbidden behaviour: Complementary LCM.
In order to charac-
terise the behaviour that is forbidden by all variants for shared activities, a
behavioural profile
B
SFB
over
A
is created as the complement of the LCM,
B
SFB
=
B
LCM
. However, this profile does not directly capture all constraints
that are not implemented in any variant due to the strictness of behavioural
relations, cf., Section 3.1. Conclusions are drawn solely from the (reverse) strict
order and interleaving order relations of the profile
B
SFB
defines in-
terleaving order between two activities, all variants show exclusiveness for these
activities. Hence, the potentially arbitrary order implied by the interleaving or-
der constraint is forbidden in all variants. Similar conclusions are drawn for
(reverse) strict order constraints in
B
SFB
.If
B
SFB
.
We illustrate this concept with the activities
'Update GBA Data'
and
'Send
Notifications'
of our initial example. For both activities, the LCM defines inter-
leaving order, which yields exclusiveness in the complement. As exclusiveness is
the strictest relation, we cannot draw any conclusions on shared forbidden be-
haviour. For the activities
'Confirm Identity'
and
'Update GBA Data'
, however,