Information Technology Reference
In-Depth Information
obviously not trivial
per se
, and these principles are here inapplicable due to the
requirement of user involvement. However, we can try to near it by progressively
narrowing the functional dependencies. Since the number of possible functional
dependencies for each entity types can be very high, we start from the set of
strongest
dependencies, through which each component of a given entity type
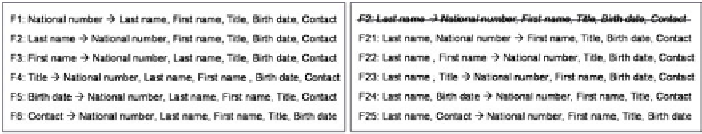
determines the other components. For instance, the form of Fig. 2 induces the
initial functional dependencies
F
1
,
F
2
,
F
3
,
F
4
,
F
5
and
F
6
of Fig. 3. From these
dependencies, we will be able to recursively generate
weaker
functional depen-
dencies to cover all the existing ones, by progressively reducing the right-hand
sides and enlarging the left-hand sides. The objective is to favour functional
dependencies with minimal left-hand sides and maximal right-hand sides.
Fig. 3.
The initial functional dependencies
F
1
,
F
2
,
F
3
,
F
4
,
F
5
and
F
6
for form of Fig. 2,
as well as alternatives for
F
2
Finally, potential
unique constraints
are induced from validated and potential
functional dependencies, using the fact that the left-hand side of a given func-
tional dependency
f
:
X
→
Y
is a potential identifier for an entity type having
the set of components
C
=
X
∪
Y
.
4.3 Analysing New Data Samples to Suggest Constraints and
Dependencies
Once the sets of constraints and dependencies have been initialised, we take
advantage of user input to acquire data samples that will progressively reduce
the set of potential constraints and dependencies. To be consistent with the
previously validated constraints and dependencies, any new tuple must respect
the latter to be accepted. Once a new tuple is acceptable, we proceed with
its analysis to determine which potential constraints and dependencies do not
hold any more. The invalidated constraints are discarded, while the invalidated
functional dependencies are replaced by alternative dependencies. Let us explicit
this process for each type of constraint and dependency when adding a new valid
tuple. Fig. 4 illustrates three data samples that could be encoded for the form of
Fig. 2, and Fig. 5 illustrated the underlying relation
Person
after the acquisition
of these data samples. Despite the apparent structure of attribute
Contact
,this
relation is in 1NF. Indeed, the compound value must be considered as a whole
whose unique goal is to reference a target tuple in the
CONTACT
table.
First of all, discarding the potential
domains of value
and
cardinalities
that
do not hold any more is relatively straightforward, since it consists in removing