Information Technology Reference
In-Depth Information
q
1
0
q
1
use
R
1
use
R
2
use
R
1
use
R
2
q
2
q
2
q
1
q
1
use
R
2
use
R
1
use
R
2
use
R
1
use
R
2
use
R
1
q
3
q
3
q
2
q
2
(a)
A.
(b)
B.
(c)
C.
(d)
D.
q
1
,q
1
,q
1
,q
1
use
R
1
use
R
2
q
2
,q
1
,q
2
,q
1
q
1
,q
2
,q
1
,q
2
use
R
2
use
R
1
use
R
2
use
R
1
q
3
,q
1
,q
1
,q
1
q
2
,q
2
,q
2
,q
2
q
1
,q
3
,q
1
,q
1
use
R
2
use
R
1
q
3
,q
2
,q
1
,q
2
q
2
,q
3
,q
2
,q
1
use
R
1
use
R
2
q
3
,q
3
,q
1
,q
1
(e)
S
0
.
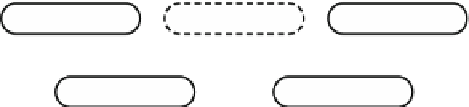
Fig. 1.
Example 1. 1a-1b) Robot automata
A
and
B
, 1c-1d) resource automata
C
and
D
,and(1e)
a supervisor candidate
S
0
.
A
1
B
1
q
q
A
R
1
v
B
=
B
R
2
v
C
=
use
use
use
R
1
use
R
2
2
1
q
q
A
2
B
2
q
q
C
1
D
1
q
q
A
R
1
v
B
=
B
R
2
v
C
=
use
use
A
R
2
B
R
1
use
use
2
1
q
q
R
2
R
1
use
use
A
3
B
3
q
q
C
2
D
2
q
q
(a)
A.
(b)
B.
(c)
C.
(d)
D.
Fig. 2.
Guards representing the behavior of the supervisor for Example 1