Information Technology Reference
In-Depth Information
1. Put the device in the DFU mode. You can do this by selecting the menu item
1
and following the onscreen instructions.
2. After the device has been put in the DFU mode, load the ramdisk with the acquis-
ition tools by selecting menu item
2
or answer
y
to the prompt that follows the
DFU procedure. It automatically detects the type of the device and loads the com-
patible ramdisk onto it. When ramdisk is successfully loaded, the device screen
will show the Elcomsoft logo.
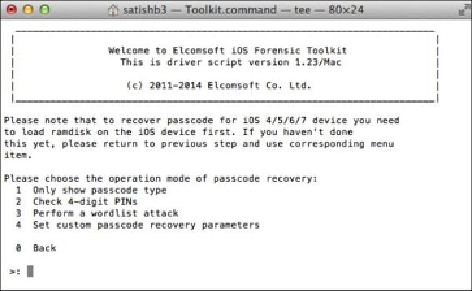
3. Recover the device passcode by selecting menu item
3
. The toolkit can recover a
simple 4-digit passcode in less than 20 minutes. It also provides options to per-
form dictionary (wordlist) and brute force attacks on complex passwords, as
shown in the following screenshot:
The EIFT passcode recovery options
4. Extract the encryption keys required to decrypt files and keychain items by select-
ing menu item
4
. You will be prompted to supply the device passcode, if known,
of the escrow file if you have access to the host computer and a filename to save
the keys. If the filename is not supplied, the toolkit extracts the keys and stores it
in the
keys.plist
file in the user's home directory.
5. After extracting the keys, to decrypt the keychain items, select menu item
5
. The
toolkit uses the keys stored in the
keys.plist
file, decrypts the keychain
items, and stores it in the
keychain.txt
file in the user's home directory.
6. To acquire the physical image of the device's file system, select the menu item
6
.
You will be prompted to choose the device partition (system and user data) to im-
age, as shown in the following screenshot: