Cryptography Reference
In-Depth Information
the edge of an active volcano, they are easily susceptible to capture by a foreign agent.
In case of a battlefield scenario, the enemy could make an effort to dig into nodes
with the intention of extracting useful data (extracting private keys in sensor nodes).
Furthermore, it could be reprogrammed and launched into a battlefield to operate on
behalf of the enemy.
2.2.4 Attacks Specifi c to WSN
2.2.4.1 Attacks on TinyOS Beaconing Protocol
TinyOS Beaconing Protocol uses a breadth-first spanning tree algorithm to broadcast
routing updates. The sink node periodically broadcasts updated routing information to
its immediate neighboring nodes. These neighboring nodes then rebroadcast this infor-
mation to their immediate neighbors, and the process continues recursively. During
this process, each intermediate node makes a note of its parent node (the parent node
is the first node that was able to make contact with its subordinate node and relay the
routing information). When all the active nodes are operational, they should send all
the sensed data to their parent node. However, this protocol is vulnerable to many
attacks. For example, a simple impersonation attack, leading to a sinkhole attack, can
totally compromise the entire network (Karlof and Wagner 2003; Sun et al. 2008).
Authentication can be used to prevent such impersonation attacks, but it does not
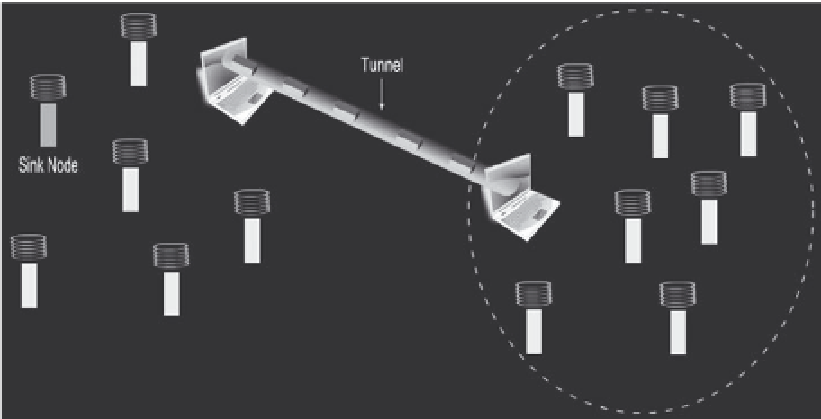
prevent a laptop-class adversary from launching a selective forwarding attack (Figure
2.5), an eavesdropping attack, or a black-hole attack. The attacker creates a wormhole
between two conniving laptop-class adversaries. The two laptops are placed near the
sink node and the targeted area, respectively. The laptop near the sink node attracts its
Figure 2.5.
Selective Forwarding Attack in TinyOS Beaconing





























Search WWH ::

Custom Search