Cryptography Reference
In-Depth Information
cryptography to implement many security protocols, its use in IBC protocols helps pro-
vide practical secure solutions to resource-constraint environments such as WSN. As
mentioned in Chapter 4, IBC is a public key technique that is based on the identities of
entities. In the WSN environment, the sensor node's identity can be used as the public
key. Hence, there is no need for a certificate to bind a sensor node's identity to its public
key. Therefore, IBC provides practical public key cryptographic schemes (authentica-
tion, encryption, or session key setup) without the use of a complex public key infra-
structure. In many ways, an identity-based scheme is an appropriate solution for sensor
networks. There is no need to maintain a public key directory, as the public keys can
be derived from node identities that are widely known in the network. IBC provides a
scalable security mechanism in which the number of keys is kept to a minimum. Nodes
generate a public key for a given node only when they want to communicate with it for
the first time. After agreeing upon a shared session key, nodes can use symmetric key
mechanisms to encrypt subsequent messages and to communicate in a secure manner.
IBC allows every node to send secure messages to all the other nodes from the
beginning of the network operation. No prior interaction between the nodes is needed.
Exchange of the information does not require any service or assistance from a third
party. However, identity-based systems assume the existence of a trusted key-generation
center, which issues private keys corresponding to user identities. This authority can
use its master key to decrypt user messages. It can also impersonate anyone in the
network. This feature introduces the key escrow problem, wherein the security of the
whole system depends on the public key generator security. In many cases, a single
unconditionally trusted entity in the network simply does not exist. Fortunately, in
sensor networks the original network deployer can be considered as a trusted entity that
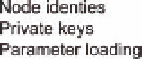
can act as the public key generator. It can generate a unique secret key based on each
node's identity and pre-load this information to the node's memory before the deploy-
ment phase. At this stage, a secure channel clearly exists which allows careful configu-
ration of the network. The application of IBC to WSN is presented in Figure 9.1.
Figure 9.1.
Identity-Based Cryptography in WSN












































Search WWH ::

Custom Search