Cryptography Reference
In-Depth Information
heads join the cluster using one-hop transmission. As in LEACH, each node deter-
mines a random number and compares it with the threshold
T
(
n
) in the current round
to gauge if it would be elected to be a cluster head.
7.4.1.3 Security Vulnerabilities in Cluster-Based Routing Protocols
Similar to any routing protocol in WSN, cluster-based routing protocols (LEACH-
like protocols) are susceptible to many security attacks. As these protocols depend on
cluster heads, attacks on cluster heads could be more detrimental than on ordinary
sensor nodes.
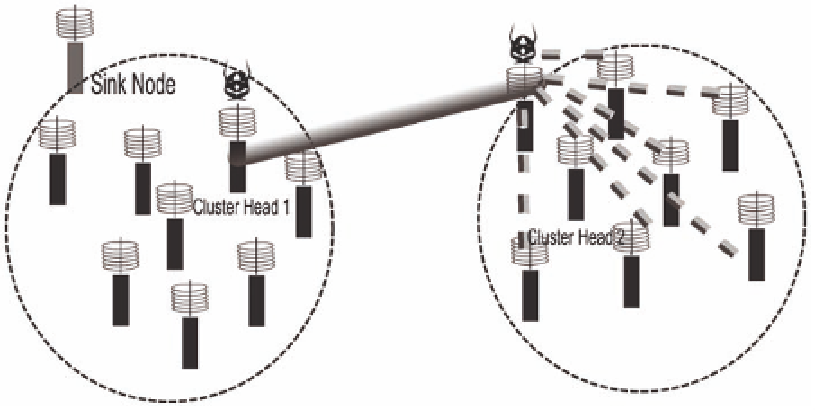
If an attacker is able to compromise and impersonate a cluster head, it can provoke
attacks, such as a man-in-the-middle, black hole, or selective-forwarding attack (Figure
7.4), thus compromising the entire network.
For example, a simple impersonation attack leading to a sinkhole attack could
totally compromise the entire network in a cluster-based hierarchical architecture
(Section 2.2.2 ).
In the traditional Public Key Infrastructure (PKI)-based architecture (Section 4.2),
the compromised cluster head in cluster 1 immediately relays information about its
revoked key to all of its immediate neighbors. Let us consider the case where a rogue
sensor node is one of its immediate neighbors and is a resource-abundant device. This
rogue sensor node in cluster 1 will tunnel the revoked key information to its colluder
in cluster 2, even before the compromised cluster head in cluster 1 informs its peer in
the other cluster. Now, the resource-abundant adversary in cluster 2 can impersonate
the cluster head in cluster 1 and generate a new public key as it is aware of the compro-
mised private key. It can reauthenticate to the cluster head in cluster 2 and all the sensor
nodes in cluster 2. After proving its authenticity, it can launch a selective-forwarding,
Figure 7.4.
Selective-Forwarding Attack in WSN





























Search WWH ::

Custom Search