Cryptography Reference
In-Depth Information
Then, the probability that no key is shared between any two rings is
t
2
/
t
1
. Hence, the
probability
p
is
2
t
((
Q
-
m
)!)
=- =-
2
p
1
1
(6.4)
t
Q
!(
Q
-
2
m
)!
1
Usually, the value of
p
is ver y large in comparison to
m
, and using the Sterling's approxi-
mation for
n
!, the value of
p
is
2(
Qm
-+
0.5)
æ ö
÷
m
Q
ç
-
ç
ç
÷
1
÷
ç
è ø
=-
æ
p
1
(6.5)
(
Qm
-+
2 . )
ö
÷
2
m
Q
ç
÷
1
-
ç
÷
ç
÷
ç
è
ø
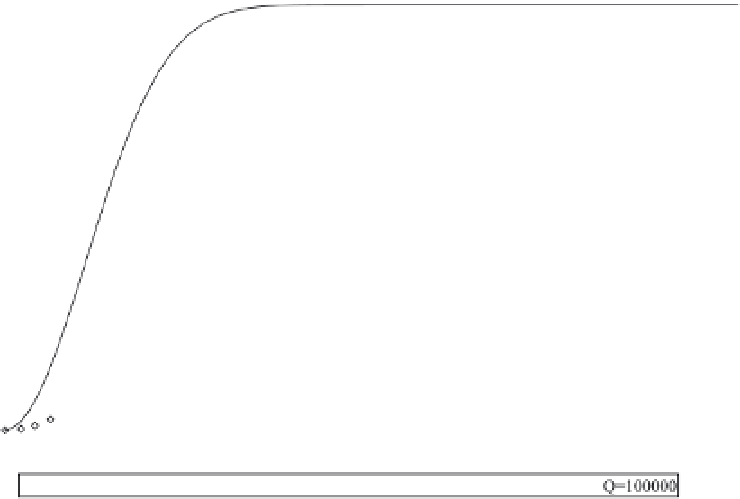
Figure 6.1 shows the value of
p
for different values of
Q
and
m
. We observe that with
the increase in
Q
, there is a negligible increase in the key ring size
m
for the same value
of
p
. For example, for
p
= 0.5 and
Q
= 6000, the value of
m
= 68. Subsequently, if the
pool size is increased to 10,000, for the same value of
p
= 0.5,
m
is only increased to 95.
In this scheme, all nodes use the same key pool
Q
. This implies that the security of
the network is gradually eroded as keys from
Q
are compromised by an adversary that
captures more and more nodes. In this scheme, the number of exposed keys is roughly
Figure 6.1.
Probability of Sharing At Leas
t One Shared Key Using Eschenauer and
Gligor's Scheme


































































































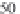



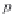

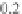
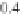










































































































































Search WWH ::

Custom Search