Hardware Reference
In-Depth Information
Up = 0.69
50
45
Background
Polling
SS
Slack Stealer
40
35
30
25
20
15
10
5
0
5
10
15
20
25
Average aperiodic load
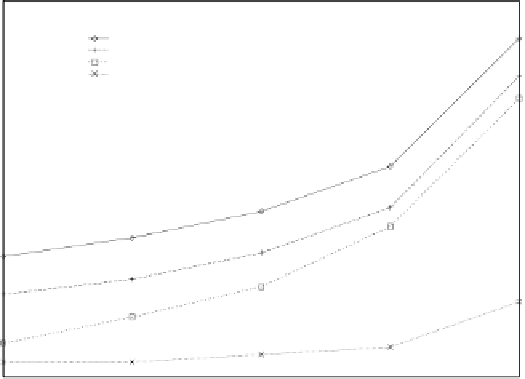
Figure 5.25
Performance of the Slack Stealer with respect to background, PS, and SS.
Figure 5.25 shows the performance of the Slack Stealing algorithm with respect to
background service, Polling, and SS. The performance of DS and PE is not shown
because it is very similar to the one of SS. Unlike the previous figure, in this graph
the average response times are not reported relative to background, but are directly
expressed in time units. As we can see, the Slack Stealing algorithm outperforms
all the other scheduling algorithms over the entire range of aperiodic load. However,
the largest performance gain of the Slack Stealer over the other algorithms occurs at
high aperiodic loads, when the system reaches the upper limit as imposed by the total
resource utilization.
Other simulation results can be found in Lehoczky, Sha, and Strosnider [LSS87] for
Polling, PE, and DS, in Sprunt, Sha, and Lehoczky [SSL89] for SS, and in Lehoczky
and Ramos-Thuel [LRT92] for the Slack Stealing algorithm.
5.10
SUMMARY
The algorithms presented in this chapter can be compared not only in terms of per-
formance but also in terms of computational complexity, memory requirement, and
implementation complexity. In order to select the most appropriate service method












Search WWH ::

Custom Search