Information Technology Reference
In-Depth Information
3. The user's browser requests the logon page from the federation proxy server.
4. The user enters logon credentials, and the federation proxy server passes them to the feder-
ation server in the internal network.
5. The federation server validates the credentials with a directory server, such as AD LDS.
6. The federation server receives credential information from the directory service and creates
the security token.
7. The security token is passed back to the client with the URL of the application on the ADFS-
enabled Web server.
8. The client presents the security token to the Web server and accesses the application.
Federated Web SSO
The
federated Web SSO
design is similar to Figure 12-5, in which
a trust relationship is established between the resource partner and the account partner. A fed-
eration server is running on both networks. Although not shown in the figure, federation proxy
servers are often used in this design to enhance security. The Web SSO design is inherent in this
design, where Internet users who aren't part of the trust can still access Web applications in the
resource partner network. In this situation, the account partner users request Web services from
the resource partner. The resource partner doesn't authenticate the user locally, but redirects the
user back to the federation server in the account partner network. The account federation server
validates the credentials and creates a security token for the client to present to the resource fed-
eration server. The federation server creates a security token for the client to present to the
ADFS-enabled Web server, and the client requests the application. The federated Web SSO design
supports business-to-business relationships for collaboration or commerce purposes.
Federated Web SSO with Forest Trust
The
federated Web SSO with forest trust
design involves a network with two Active Directory forests. One forest, located in the perimeter
network, is considered the resource partner. The second forest, located in the internal network, is
the account partner. A forest trust is established between domain controllers in both forests. In
this design (see Figure 12-7), internal forest users and external users have access to ADFS-enabled
Web applications in the perimeter network. External users have Active Directory accounts in the
perimeter forest, and internal users have accounts in the internal forest. This design is used most
often when Windows NT token applications are hosted on the Web servers. The AD FS Web agent
running in the perimeter network intercepts authentication requests and creates the NT security
12
Perimeter
forest
Internal
forest
ADFS-enabled
Web server
Federation trust
Account
federation
server
Internet client
Resource
federation
server
Forest trust
AD DS
internal
forest
AD DS
perimeter
forest
Niftytools.com
Figure 12-7
The federated Web SSO with forest trust design





























































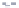





















Search WWH ::

Custom Search