Information Technology Reference
In-Depth Information
Choosing a Single or Multiple Forest Design
Most organizations operate under a
single Active Directory forest, which has a number of advantages:
•
A common Active Directory structure
—Forestwide replication and a single schema for the
forest provide a consistent, reliable directory service.
•
Easy access to network resources
—The global catalog and forestwide trusts make finding
and accessing resources across domains easy.
•
Centralized management
—A single administrative unit to manage all aspects of the direc-
tory simplifies administering and implementing network policies.
Ironically, the advantages of a single forest structure entail limitations that might lead an
organization to design its Active Directory structure around multiple forests. Some large organ-
izations can consist of a collection of diverse business units. Companies merge, are taken over,
reorganize, open foreign offices, and so forth, creating what amounts to several businesses under
the umbrella of a single corporation. Each business unit might have widely differing management
policies and be running different business applications. Having this amount of diversity with a
single Active Directory forest often requires a high level of cooperation or might be technically
unfeasible. Some reasons, technical and administrative, that a company might choose a multiple
forest design include the following:
•
The need for differing schemas
—For example, when two businesses merge, each might
have an existing Active Directory structure with customized schema elements that are
incompatible with one another.
•
Security boundaries
—By default, directory information in one forest isn't accessible, or
even visible, to users in a different forest, which makes the forest a security boundary.
However, trusts can be configured between domains in different forests so that administra-
tors can control cross-forest access.
•
Separate administration
—When multiple business units have separate IT administration,
there might be disagreement on policies that affect the entire forest. Whether differences
are technical or political, a multiple forest design could be the best solution.
Organizations that do use multiple forests usually must configure trusts between the forests,
as you learn in the following section.
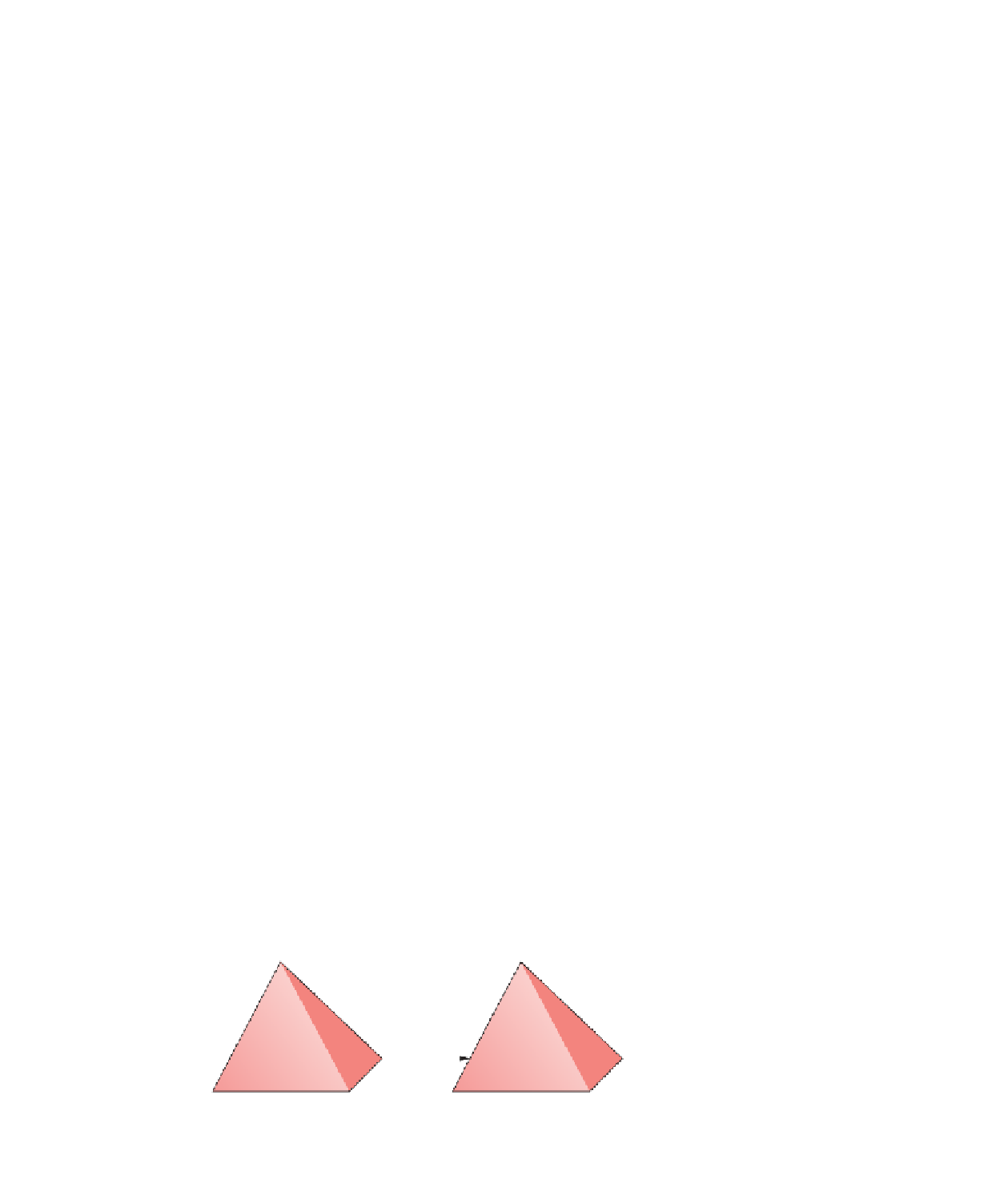
Active Directory trusts can exist between domains and between forests. With a trust relationship
between domains in the same forest or in different forests, users can access resources across
domains without having to log on more than once. Moreover, a user account needs to exist in
only one domain, which simplifies user management.
To say that Domain A trusts Domain B means that users in Domain B can be given permis-
sion to access resources in Domain A. Domain A is referred to as the trusting domain, and
Domain B is referred to as the trusted domain. In Active Directory design documentation, a trust
relationship is drawn with an arrow pointing from the trusting domain to the trusted domain, as
shown in Figure 4-13. There are a number of trust relationship types, explained in the following
sections: one-way and two-way trusts, transitive trusts, shortcut trusts, forest trusts, external
trusts, and realm trusts.
Domain A trusts
Domain B
Domain A
Domain B
Trusting domain
Trusted domain
Figure 4-13
A trust relationship
Search WWH ::

Custom Search