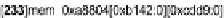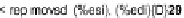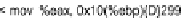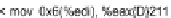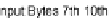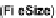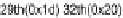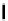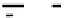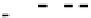Information Technology Reference
In-Depth Information
With the dynamic analysis techniques provided by TREE/CBASS, we are able to
answer the aforementioned questions in a few minutes. More specifically, the tool can
generate a trace that leads to the crash. Furthermore, it can replay the trace by first
marking the whole 68 bytes of the file as the taint sources, and then stopping at the
tainted points. From the taint graph, we are able to see the connection between the
instruction that caused the crash (call
eax
where
eax = 0xa8b94
) and some of the file
structures. We have identified 12 unique instructions in WMF that are directly related
to moving and processing the file and causing the application to crash. Since our tool
can generate an interactive graph, the user can navigate along the chained data and
instructions by clicking on each tainted node in the graph.
Fig. 8 shows part of the WMF crash taint graph. The right side is a snapshot taken
from the TREE GUI. The nodes in green show the taint source bytes (WMF file), and
the nodes in red show the bytes pointed by
eax
in the
call eax
instruction that caused
an exception. The left side of the figure shows some internal text representation of the
taint graph. For example, the node
355
shows the tainted node of
0xa8b94
. Following
the
D
link (highlighted in bold), we can see that it is data-dependent on node 233, which
in turn is data-dependent on node 29, an input byte that corresponds to part of the
shell-code section. Following the
C
link (highlighted by underline), we can see that it
is affected by a loop whose iteration number depends on the values from the 7th to the
10th bytes in the WMF file. When looking back at the
WMFHead
structure, we find that
bytes 7-10 actually correspond to the
FileSize
field.
Fig. 8.
Case Study: The WMF Crash and Taint Graph