Information Technology Reference
In-Depth Information
- critical event
- monitor invocation (ET)
- monitor invocation (TT)
- mode switch (ET to TT)
- mode switch (TT to ET)
- 'redundant' sample
frequent monitor
activity
1
i
j
n
time
(a) Event-triggered monitoring.
SP
1
i j
(b) Time-triggered monitoring.
n
time
1
i j
(c) Hybrid monitoring.
n
time
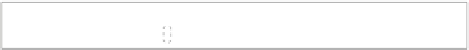
Fig. 1.
Comparing different methods of monitoring
verification is to contain its runtime
overhead
. Most monitoring approaches in
the literature are
event-triggered
(ET), where the occurrence of a new (critical)
event (e.g., change of value of a variable) triggers the monitor to verify a set
of logical properties. For example, in the timing diagrams in Figure 1(a), the
dots 1 through
n
along the timeline represent the critical events that occur for
an execution trace of the program under scrutiny at run time. The calls to the
monitor are added as instrumentation instructions in the program. As shown
in the figure, there is a burst of events in this execution trace from event
i
to
event
j
. The frequent monitor invocations that occur from
i
to
j
leads to a
burst of monitoring, which causes high execution overhead and unpredictability
of program behavior.
In [2,3], we introduced a
time-triggered
(TT) method that makes the runtime
overhead controllable and predictable, and makes monitoring tasks schedulable.
In this method, a monitor samples the state of the program in periodic time in-
tervals. The period, known as the
sampling period
(SP) is such that the monitor
misses no critical events. Time-triggered monitoring is especially desirable for
designing real-time embedded systems, where time predictability plays a cen-
tral role. Figure 1(b) shows the interactions that occur between the program
and a TT monitor. To decrease the sampling frequency and thus decrease the
overhead, we introduced a technique, where the program stores critical events
in a history buffer and the monitor reads this buffer to evaluate properties with
respect to all state changes stored in the history [2, 3]. From the figure, it is
evident that the monitoring activity between events
i
and
j
is significantly less
than what an event-triggered monitor would require. However, for the sampling
period adopted in this example, there are some 'redundant' samples that the