Cryptography Reference
In-Depth Information
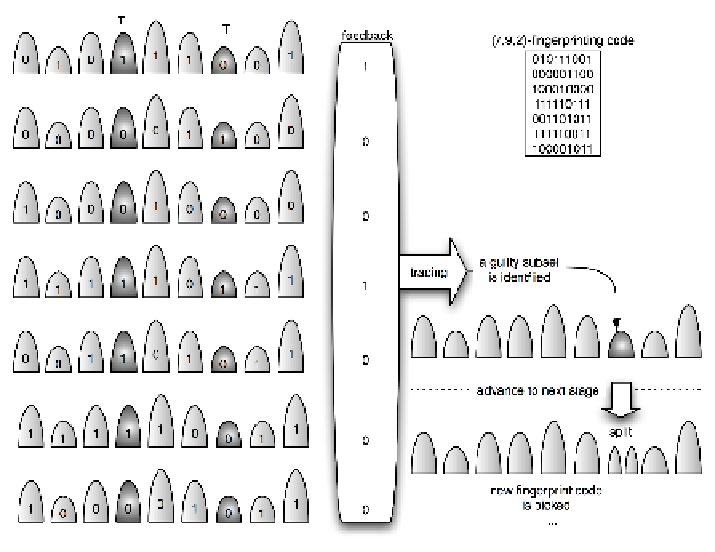
Fig. 4.3. Illustration of tracing and revoking a pirate rebroadcast. In this example,
the revocation instruction ψ has 9 subsets and a code of length 7 is used over a
binary alphabet.
from the state. After a su
cient number of transmissions (that matches the
length of the code) the sequence of pirate rebroadcasts will form a pirate code-
word and by applying the identify algorithm of the fingerprinting code on it
we will identify a subset that contains at least one traitor. This is because
of the fact that the codewords of
F
are assigned to subsets of receivers, i.e.,
the detection of a “traitor” from the Identify algorithm is now equivalent to
finding a subset that contains a traitor. This constitutes the progress that is
necessary for winning the revocation game. Moreover observe that this subset
may be split into 2 subsets or more depending on the properties of the under-
lying subset cover scheme and the process be repeated. The updated set of
users, i.e the subsets in the new partition, will be reassigned new codewords
from possibly a fresh fingerprinting code. Observe that the Identify algo-
rithm of the fingerprinting code substitutes the “walking” argument that was
employed in the previous section that progressively randomized the pattern
ciphertext untill a position is identified that the adversary fails to decrypt
successfully. This mechanism was the the basic procedure which tests a pirate
box that is successful in decrypting with a given pattern by using some spe-
cial tracing ciphertexts to output a subset containing a traitor. We note that