Cryptography Reference
In-Depth Information
A
j
B
j
C
j
D
j
E
j
f
r
w
j
+
K
r
+
s
j
≪
≪ 10
A
j
+1
B
j
+1
C
j
+1
D
j
+1
E
j
+1
Fig. 1.
Step Function in PKC98-Hash
Finally, feed-forward is computed; The initial value
A
0
,
B
0
,
...
,
E
0
and the
output of the last step
A
96
,
B
96
,
...
,
E
96
are added by wordwise modular addi-
tion
2
as an output of the compression function.
2.2
Specification of HAS-V
HAS-V was proposed by Park
et al.
in [12]. It processes 1024-bit message blocks
and produces a hash value of 128 + 32
k
(
k
=0
,
1
,...,
6) bits. HAS-V also adopts
the Merkle-Damg ard structure. Again, let
M
=
M
0
M
t−
1
be a
t
-block
message (after padding). We refer to the description of the padding method
in [12]. Hash value
H
is computed by the iteration of compression function
CF :
M
1
···
320
1024
320
using the recurrence
H
i
+1
←
{
0
,
1
}
×{
0
,
1
}
→{
0
,
1
}
CF(
H
i
,M
i
)
(
i
=0
,
1
,...,t
1) where
H
0
is a predefined initial value. Compression function
CF updates chaining value
H
i
in two-parallel lines (left and right) adopting
the Davies-Meyer structure where the intermediate values of the two lines are
swapped at the end of each round.
−
Message Schedule.
A 1024-bit input
M
i
is divided into two 512-bit blocks
X
Y
←
M
i
, and then divided into 2 sets of sixteen words,
X
0
X
1
···
X
15
←
X
Y
0
Y
1
···
Y
15
←
Y
We denote expanded messages to compute step
j
of the left and right com-
pression functions by
w
j
and
w
j
, respectively. The index of
w
j
and
w
j
are
identical and determined by Table 3, where
w
j
and
w
j
for
j
=16
,
17
,
18
,
19
are computed by XOR of 4 message words indexed by Table 4.
2
There is no description of this operation in the original paper. We can interpret
it as XOR instead of the modular addition. However, this choice is not important
because the best proposed attack can work in both cases. As an independent interest,
in Section B.2, we show an attack that works well for addition feed-forward, but not
for XOR.






















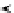












Search WWH ::

Custom Search