Cryptography Reference
In-Depth Information
C An Overall View of Our Related-Key Rectangle Attack
0
0
80
ͷ
͡
0
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
ͷ
͢
ͷ
͡
0
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
10
0
0
0
0
0
0
80
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
0
80
80
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
10
0
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
68
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
10
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
0
80
E0
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
2
-12.017
10
0
80
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
E1
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
2
-40.381
68
0
ℬ
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͢
10
0
80
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
0
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͢
10
00
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
68
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
10
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
0
0
0
0
0
0
0
10
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
0
0
0
0
0
0
10
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
0
0
0
0
68
0
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
0
0
0
10
0
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
0
ℱ
0
0
ͷ
͡
ͷ
͢
ͷ
͡
ͷ
͢
10
ℰ
0
0
Fig. 5.
Related-key differential trails of HIGHT

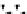



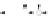

















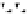


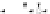
















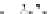
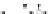

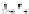
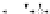

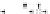



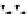
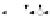


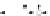


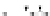


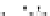

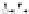
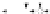

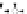


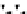

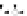


















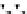


















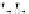












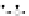











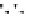











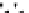

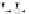






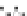

















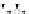














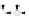






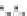















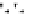

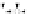



















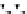




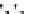

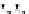











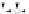






















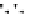















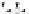



















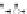






























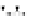






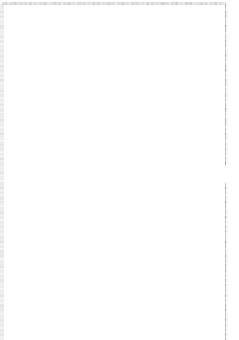























































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































































Search WWH ::

Custom Search