Cryptography Reference
In-Depth Information
a
()
0
n
a
()
1
n
a
()
2
n
Obtained
a
()
0
n
a
()
1
n
a
()
2
n
64
64
64
b
()
4
n
64
64
64
64
b
()
4
n
64
b
()
10
n
64
17
F
<<<
⊕
b
()
10
n
64
17
F
<<<
⊕
F
⊕
F
⊕
C
⊕
⊕
64
C
C
C
⊕
⊕
64
64
2
64
( )
1
n
+
( )
0
n
+
a
a
( )
2
n
+
a
( )
1
n
+
a
a
( )
2
n
+
a
( )
0
n
+
64
64
64
( )
4
n
+
64
64
64
64
b
( )
4
n
+
64
b
b
(
)
10
n
+
64
17
F
<<<
(
)
10
n
+
b
64
17
F
⊕
<<<
⊕
F
F
⊕
Obtained
⊕
Obtained
a
( ) ( )
1
n
+
+
⊕<<<
(
b
n
17)
10
C
⊕
⊕
64
C
C
⊕
⊕
64
C
64
2
2
64
( )
0
n
+
( )
1
n
+
a
a
a
( )
2
n
+
( )
0
n
+
( )
1
n
+
a
a
a
( )
2
n
+
64
64
64
64
64
64
b
( )
4
n
+
64
b
( )
4
n
+
64
(
)
10
n
+
b
64
17
b
(
)
10
n
+
<<<
F
64
17
F
<<<
⊕
⊕
F
F
⊕
⊕
Obtained
( ) ( )
1
a
n
+
⊕
(
b
n
+
<<<
17)
10
C
⊕
⊕
64
C
C
⊕
⊕
64
C
64
2
64
2
a
( )
0
n
+
a
( )
1
n
+
( )
0
n
+
( )
1
n
+
a
( )
2
n
+
a
a
a
( )
2
n
+
(a) When 8 bytes of
a
(
n
)
2
a
(
n
+1)
2
are corrupted
(b) When 8 bytes of
are cor-
rupted
Fig. 3.
Known values are shown in the heavy line and the known states are indicated
as diagonal lines
In the above equation,
y
l
(
l
=0
,...,
7) is the
l
-th byte of
y
and
Δ
(
n
)
(
l
=0
,...,
7)
l
is the
l
-th byte of
Δ
(
n
)
(
n
=
t,...,t
+5).
S
is the S-box table and
M
−
1
is the
inverse of the matrix
M
.
Since
Δ
(
n
)
and
Δ
(
n
+1)
are known values, the attacker can solve the above
equation and obtain the candidates for
a
(
n
+1)
1
(
b
(
n
+1)
10
≪
17
)(
n
=
t,...,t
+5).
The number of the solutions to (2) is 2 at 99.2% probability and 4 at 0.8%
probability as shown in Appendix A.
In order to determine uniquely the solutions for (2), the attacker injects an-
other 8-byte fault into the same location,
a
(
n
2
. Similarly, he obtains the can-
didates for
⊕
a
(
n
+1)
1
(
b
(
n
+1)
10
}
l
(
l
=0
,...,
7
,n
=
t,...,t
+5) by solving
the equation for the S-box. At this point, the attacker finds that one solution is
the same as the solutions for (2) with 98.8% probability as shown in Appendix
B, then, he finds
{
⊕
≪
17
)
a
(
n
+1)
1
(
b
(
n
+1)
10
}
l
(
l
=0
,...,
7
,n
=
t,...,t
+5). From
Sec.6.4, the attacker can obtain 8 bytes of
a
(
n
+1)
1
{
⊕
≪
17
)
(
b
(
n
+1)
10
≪
17
)(
n
=
t,...,t
+5)
using 2.09 pairs of correct and faulty outputs on average.
Since the attacker knows
a
(
n
+1)
1
⊕
(
b
(
n
+1)
10
⊕
≪
17
)(
n
=
t,...,t
+5), he also
knows
a
(
n
1
(=
a
(
n
+1)
)(
n
=
t,
···
,t
+ 5) by the characteristics of the
ρ
-function
0
shown in Fig.3 (a).























































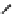



































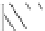



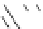


















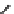
















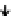















































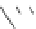










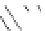

















































Search WWH ::

Custom Search