Cryptography Reference
In-Depth Information
()
1
t
()
2
t
a
()
0
t
a
a
64
64
64
()
4
t
64
b
()
10
t
b
64
17
F
<<<
⊕
F
⊕
C
⊕
⊕
64
C
64
(
0
t
+
1
a
a
(
1
t
+
1
(
2
t
+
1
a
64
64
64
(
4
t
+
1
64
b
b
(
10
t
+
1
64
17
F
<<<
⊕
F
⊕
C
⊕
⊕
64
C
64
(
0
+
t
2
)
a
a
(
1
t
+
2
)
a
(
2
t
+
2
)
64
64
64
(
4
t
+
)
2
64
b
b
(
10
t
+
2
)
64
17
<<<
F
⊕
F
⊕
C
⊕
⊕
64
C
64
(
0
t
+
3
)
a
a
(
1
t
+
3
)
(
2
+
t
3
)
a
a
(
t
)
2
Fig. 2.
Fault propagation when 8 bytes of
are randomly corrupted. The fault
propagation is shown as dotted lines.
is affected by a fault propagated to
a
(
t
+2
0
in round (
t
+2) shown in Fig.2 because
the
λ
-function uses
a
0
as a parameter. However, this fact is not a problem for
the attack.
The attacker can obtain the values of faults by calculating the difference
between correct output,
a
(
n
2
, and faulty output,
a
(
n
2
(
n
=
t,...,t
+5). Here, we
define the difference between correct and faulty outputs in round
n
as
Δ
(
n
)
(=
a
(
n
)
2
a
(
n
2
)(
n
=
t,...,t
+5).
When the fault is injected into
a
(
n
2
, the equation for the difference of the
S-box table in round (
n
+ 1) is expressed as
⊕
a
(
n
+1)
1
(
b
(
n
+1)
10
a
(
n
+1)
1
(
b
(
n
+1)
10
Δ
(
n
)
l
S
[
{
⊕
≪
17
)
}
l
]
⊕
S
[
{
⊕
≪
17
)
}
l
⊕
]=
y
l
(2)
y
=(
y
0
||y
1
||y
2
||y
3
||y
4
||y
5
||y
6
||y
7
)
=
M
−
1
(
Δ
(
n
+1)
4
||Δ
(
n
+1)
5
||Δ
(
n
+1)
2
||Δ
(
n
+1)
3
)
|| M
−
1
(
Δ
(
n
+1)
0
||Δ
(
n
+1)
1
||Δ
(
n
+1)
6
||Δ
(
n
+1)
7
)
































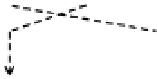




















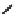



















Search WWH ::

Custom Search