Cryptography Reference
In-Depth Information
a) Strategy 1: Encoding P
i,j
Q
i,j
×
F
type I.a
128 x 128 128 x 8
b) Strategy 2: Encoding Q
i,j
P
i,j
8x8
Δ
1
Δ
1
Q
i,j
×
F
type I.a
type II
128 x 128
128 x 8
T'
i,j
Round 1
P
i,j
8x8
IMC'
1
type II
Q
i,j
T'
i,j
type III
8x8
IMC'
1
P
i,j
Δ
2
× Δ
−
1
1
8x8
type III
Q
i,j
Δ
2
× Δ
−
1
1
8x8
type II
T'
i,j
Round 2
P
i,j
8x8
IMC'
2
Q
i,j
type II
T'
i,j
type III
8x8
IMC'
2
Δ
3
× Δ
−
1
2
Q
i,j
type III
P
10
i,j
8x8
8x8
Δ
10
× Δ
−
1
9
Round 10
type II
T'
10
i,j
P
10
i,j
type II
Δ
−
1
10
8x8
type I.b
G
128 x 8
T'
10
i,j
Δ
−
1
10
G
type I.b
128 x 8
Fig. 2.
Encoding The Mixing Bijections































































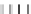











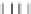

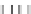


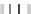






































Search WWH ::

Custom Search