Cryptography Reference
In-Depth Information
The rounds' boundaries are also modified. Let a round begin with the
T
-boxes
computations followed by
InvMixColumns
and finally
InvShiftRows
. Under this
condition, the last round does not contain any
InvMixColumns
operation.
in
Linear mapping
128x8
in
out
out
out
out
out
out
out
out
Type I
in
P
i,j
T
i,j
MB x IMC
i
32x8
8x8
in
out
out
out
out
out
out
out
out
Type II
in
Q
i,.
×
MB
−
1
32 x 8
in
out
in
in
out
out
out
out
out
out
out
out
Type III
Type IV
Fig. 1.
Mixing Bijection Tables
The next step is to compose each table with random bijections. A mixing
bijection
P
i,j
8matrixin
GF
(2)) is inserted before the
T
-boxes
T
i,j
(8
×
and an
ane bijection
MB
(32
×
32 matrix in
GF
(2)) is inserted after
InvMixColumns
step (type II table).
MB
is a non-singular matrix with 4
×
4 sub-matrices of
full rank. The mixing bijections of the next round
P
r
+1
i,j
and the ane bijection
of the current round
MB
are inverted (resp.
Q
i,j
and
MB
−
1
) and combined in
an additional set of look-up tables (type III). In order to avoid large look-up
tables, the mapping
MB
−
1
is split into four blocks, just like
InvMixColumns
matrix. The XORs are computed by type IV tables. Finally, the external input
and output encodings are implemented. It consists in selecting two 128
×
128
mixing bijection matrices
F
and
G
, defined over
GF
(2), whose all aligned 4
4
sub-matrices are of full rank. Multiply
F
by the inverted input mixing bijections
of the first round (i.e.
Q
i,j
,i
×
[0
..
3]), then insert the resulting bijection
F
prior to the first round.
G
is inserted after the last
∈
[0
..
3]
,j
∈
step. The
AddRoundKey
external encodings are implemented in type I tables.
3 Known Attacks
3.1 Billet et al. Attack
In the following, we list the different steps of the attack and their complexity. We
refer the reader to [4] for more details. Instead of locally inspecting the tables,
Billet et al. looks at the input and the output of the composition of the tables for





































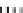

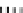

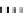


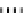


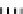
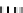
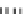



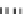

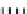
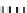
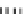



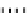
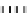


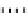





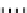
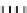













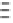



Search WWH ::

Custom Search