Cryptography Reference
In-Depth Information
9
x
10
500
15
Mean
99%
450
SN
HYBR
DHT
400
350
10
300
250
200
5
150
100
50
0
0
(a) Latency measurement
(b) Control cost measurement
Fig. 1.
The evaluation results under normal operations. Figure (a) depicts the mean notification
time and the completion time for 99% of the nodes and for different control plane mechanisms.
Figure (b) presents the total network cost in terms of bytes for the test duration of 600 seconds.
5.1
Evaluation Metrics
To evaluate the reliability and efficiency of the different control plane mechanisms, we
introduce three metrics:
coverage
,
latency
,and
control efficiency
.
Coverage
is measured
by enumerating the number of nodes that receive the alert message when the system is
under attack. Alternatively, all alert messages that are not delivered within the duration
of the experiment instance are regarded as failures.
Latency
is defined to be the period
of time that it takes for alerts to reach each participant from the moment that an alert
message is dispatched.
Control efficiency
is the cost to utilize the control mechanisms.
This is calculated by summing the total number of bytes required for network operations
during the experiment.
5.2
Evaluation Design
To validate the network behavior under adversarial conditions, we implemented three
control mechanisms using the OverSim [3] simulation framework. The use of simula-
tion was mandated for the following reasons:
Scalability.
We were interested in observing the behavior of large scale networks imple-
menting signaling systems in the presence of network-wide malicious attacks. Having
tens of thousands of number of participants, Oversim framework enabled us to quantify
the design parameters that really influence the behavior of the system.
Global Adversary.
Emulating global adversary in a real-world large-scale testbed is
a costly and time-consuming task and it does not allow repetition of experiments. The
simulation framework not only helped us to instantiate this size of network but also
provided the interface to implement a more precise behavior for the global adversary.









































































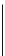




































































Search WWH ::

Custom Search