Cryptography Reference
In-Depth Information
90
900
FC HEX
FC RAW
LC HEX
LC ZRLE
FC HEX
FC RAW
LC HEX
LC ZRLE
80
800
70
700
60
600
50
500
40
400
30
300
20
200
10
100
0
0
10
20
30
40
50
6
0
70
80
90
100
110
0
20
40
6
0
80
100
120
Time (seconds)
Time (seconds)
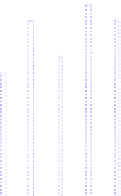
(a) CPU
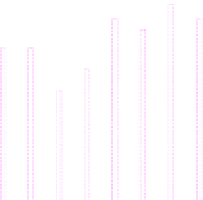
(b) Network
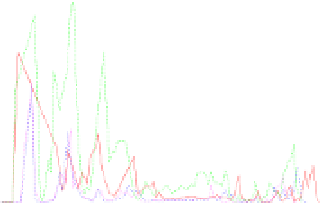
Fig. 3.
CPU and network utilization when replaying to all 96 VMs, using different
combinations of color depth and encoding schemes. RAW encoding is clearly the most
demanding. As for the low color depth ones, there is no big difference between HEX
and ZRLE.
4.2 Exfiltration Study
In order to demonstrate the threat posed by credential stealing spyware, we
conducted a study using a relatively large number of distinct samples. For the
purposes of our study, we used variations of the Zeus (also known as ZBot)
malware which is notorious for its credential stealing capabilities. All the samples
were downloaded from Zeus Tracker
4
.
In previous work, we also did provide a similar study, but somehow more
limited, as each malware sample was only active on a VM for a small amount
of time - order of a few tens of minutes. In our current study, we installed each
malware sample on a separate VM, running on the virtualized infrastructure we
built in order to simulate a thin client environment. By keeping each malware
active for a relatively long period (weeks or even months) we want to explore
two probable phenomena, not covered by our previous study. Firstly, we want
to examine whether there are malware instances that wait for a period of time
before exfiltrating the stolen credentials, and secondly, it would be interesting to
see whether instances not intended to exfiltrate, get updated in a later time to
do so. Both of these cases, if existent, would require a larger time window than
our previous study, to happen.
We bootstrapped the study by installing all the malware samples available
at the Zeus Tracker, and also we automated the procedure of installing new
samples as they are made available. In total, during the study there were 108
Zeus malware instances installed on distinct VMs running on our Dell servers
for a period of 3 to 4 weeks. During that time, we periodically injected both
Paypal and anonymous bank's bait credentials. The component that monitors
for external login attempts to the bait accounts was running for the next few
months, as login attempts can occur even months after the credentials are stolen
- based on our previous study. Along with the injections, we also monitored the


















































































































Search WWH ::

Custom Search