Cryptography Reference
In-Depth Information
16
BYTES
B
LOCK
0
B
LOCK
1
B
LOCK
2
B
LOCK
3
UID
BCC
M
ANUFACTURER
D
ATA
S
ECTOR
0
S
ECTOR TRAILER
K
EY
A
A
CCESS
C
ONDITIONS
K
EY
B
B
LOCK
60
B
LOCK
61
B
LOCK
62
B
LOCK
63
S
ECTOR
15
K
EY
A
A
CCESS
C
ONDITIONS
K
EY
B
S
ECTOR TRAILER
READ
-
ONLY
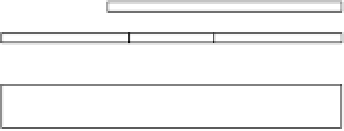
Fig. 2.
The memory structure of a Mifare Classic 1K card
that are allowed for each block of the sector (read, write, increment, decrement)
and define the role of the keys [19]. The other blocks of each sector can be used
for data storage. Note that the first block of the first sector differs from this
scheme: it always contains a UID, along with some other manufacturer-specific
data. The first block is written to the chip at manufacturing time, making it
impossible to change the UID.
When a card is placed close to a reader, the anticollision and select procedure
as defined in ISO 14443A is carried out. Then, an authentication command is is-
sued by the reader that specifies for which sector the authentication is performed.
The card replies with a 32-bit nonce
n
C
generated by its internal Pseudo-Random
Number Generator (PRNG). The reader replies with an encrypted nonce
n
R
and
an answer
a
R
, which is generated by loading
n
C
into the PRNG and clocking it
64 times. For the encryption, the keystream generated by the Crypto1 cipher is
used in groups
ks
1
,ks
2
, ...
of 32 bit each. After the card has sent the encrypted
answer
a
C
, both parties are mutually authenticated. From that point onwards,
the reader can read, write or modify blocks in the chosen sector. If another sec-
tor has to be accessed, the authentication procedure must be repeated with a
slightly modified protocol.
Reader
Card
AUTH || sector
−−−−−−−−−−−−−→
−−
32
n
C
∈
R
{
0
,
1
}
n
C
−−−−−−−−−−−−−
−−−
32
a
R
=
PRNG
(
n
C
,
64)
n
R
∈
R
{
0
,
1
}
n
R
⊕
ks
1
||
a
R
⊕
ks
2
−−−−−−−−−−−−−−−→
−
=
PRNG
(
n
C
,
64)
a
R
a
C
⊕
ks
3
−−−−−−−−−−−−−
−−−
=
PRNG
(
n
C
,
96)
a
C
Protocol 1.
The Mifare Classic authentication protocol



































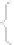


Search WWH ::

Custom Search